Exam Code: CAP
Exam Name: Certified Authorization Professional
Certification Provider: ISC
Corresponding Certification: CAP
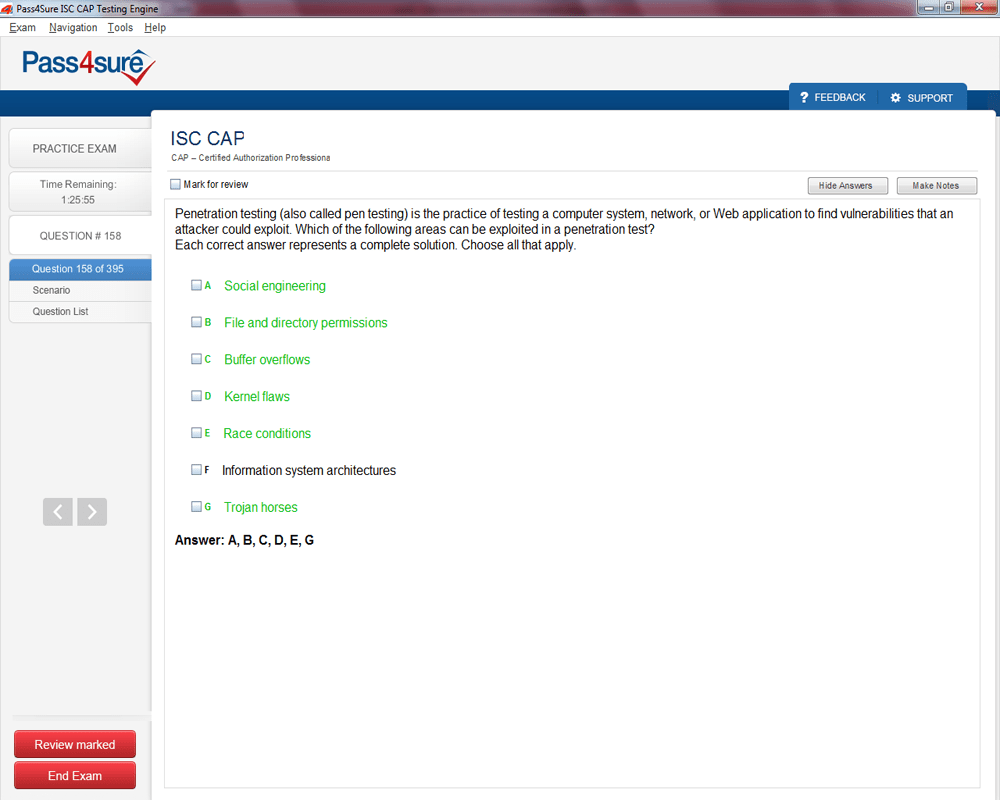
CAP Exam Product Screenshots
Product Reviews
Highly advanced preparatory materials
"Pass4sure offers highly advanced preparatory materials for CAP exam training that guarantees success. I used advanced materials of Pass4sure and cleared the CAP Certifications CAP exam with distinction. Pass4sure is a very reputable and excellent source of help for ISC CAP exam training.
Paul"
Ace CAP Exam
"The key to acing ISC CAP exam isn’t the quantity of questions that you go through but the quality. Any smart person would agree with me. I say this from experience since I recently took and passed my CAP Certifications CAP exam and definitely know what I’m taking about! Brett Goldman."
Clear CAP Exam
"Passing ISC CAP exam was as easy as taking an average exam on any other day. People make a big deal about taking CAP Certifications CAP exam and I really don’t know why! It was pretty easy for me and I passed quite easily. However, I probably only passed because I used Pass4sure products. This is Carrie Freeman."
Thanks to Pass4sure for Wonderful Product
"Thanks to pass4sure.com and the wonderful CAP exam course, I successfully passed the ISC CAP exam on May 24, 2011 on my first attempt. The pass4sure CAP Certifications CAP study guide perfectly focused on the requirements of the exam. The exhaustive collection of questions and answers made the final exam a walk in the park. After going thru more than 1000+ questions and pacing myself through sample tests, I was able to finish the final exam with time to spare and review. I highly recommend the pass4sure exam helping products to every aspiring person. Thanks pass4sure.
Joseph"
My success is credited to Pass4sure
"I took almost a full year to prep on and off for my CAP exam, and ended up using four of the popular texts & study guides (some of which were good, most of which had serious shortcomings), and also subscribed to the pass4sure ISC CAP exam kit. I have to say, of all the materials – both paid and free on the web – the pass4sure materials are, across the board, a superior corpus of learning materials and formats. Pass4sure is an extremely thorough provider of carefully constructed, well-designed, and very complete instructional materials for learning the formulas, concepts needed for the CAP Certifications CAP exam. Thanks a lot.
Jerome J."
Pass4sure preparatory material, the best solution for all exams
"When I decided to prepare for CAP exam few months back, I was finding great difficulty in getting some quality material for this exam. But Thanks to the quality products of Pass4sure that they have remedy for all the exams. I got their material and started preparation. My concepts began to improve and finally when I attempted the ISC CAP exam, I didn’t find any issue in exam questions. I passed my CAP Certifications CAP exam comfortably and just writing these words to thank Pass4sure.
Ava Atley"
Clear your concepts with pass4sure
"Exam time is the worst period of specially my life. As I was not good in my studies therefore I had to work very hard during this period. When I registered myself for CAP exams, I immediately registered on pass4sure as I wanted to start my preparation on time. Pass4sure cleared all my concepts which were unclear to me before and it also provided me with high quality notes for my ISC CAP exams preparation which helped a lot during my preparation. I was able to complete my CAP Certifications CAP exams preparation on time just because of pass4sure. I am highly obliged to pass4sure for providing me this comfort.
Clive Moore"
Pass4sure bailed me out
"I am here to admire the tremendous effort done by pass4sure team, which developed the CAP exam preparation materials. I must say that these ISC CAP study tools bailed me out of my biggest problem, which was passing my certification career, so I could step into a brighter future. Pass4sure CAP Certifications CAP study tools are very well developed and they have the answers to every question, ambiguity and problem. I can say that anyone can trust these learning notes without having an inch of hesitation and I recommend these study solutions to everyone, who wants to accomplish certification.
William Gray"
pas 4 sure had prepared me very well for the material I was expected to know.
"pas 4 sure had prepared me very well for the material I was expected to know. I found the practice questions the most beneficial. They focused on what I needed to study most. I realized that when I was taking the actual CAP exam exam. pass 4 sure had prepared me very well for the material I was expected to know.They focused on what I needed to study most. I realized that when I was taking the actual CAP exam exam. pass 4 sure had prepared me very well for the material I was expected to know.
Sheriann Wirkkala (Watt Sells winner)"
Informational material
"I would like to thanks the Pass4sure for giving me so informational CAP exam material for my ISC CAP exam. Material was excellent. For all students who are preparing to sit in the CAP Certifications CAP exam, I recommend them to buy this material instead of looking dozens of books and guides. Thanks!
Florjan"
Frequently Asked Questions
How does your testing engine works?
Once download and installed on your PC, you can practise test questions, review your questions & answers using two different options 'practice exam' and 'virtual exam'. Virtual Exam - test yourself with exam questions with a time limit, as if you are taking exams in the Prometric or VUE testing centre. Practice exam - review exam questions one by one, see correct answers and explanations.
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Pass4sure products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Pass4sure software on?
You can download the Pass4sure products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email sales@pass4sure.com if you need to use more than 5 (five) computers.
What are the system requirements?
Minimum System Requirements:
- Windows XP or newer operating system
- Java Version 8 or newer
- 1+ GHz processor
- 1 GB Ram
- 50 MB available hard disk typically (products may vary)
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.
Complete Guide to ISC Certified Authorization Professional (CAP) Certification
In the fast-moving sphere of technology, the significance of risk-centered thinking cannot be overstated. Every organization that operates within the digital realm faces uncertainties that could potentially undermine its operations. The Certified Authorization Professional is expected to approach these uncertainties not as uncontrollable threats but as manageable elements within a structured framework. This mindset cultivates foresight, balance, and the ability to establish calculated safeguards that protect critical information assets while still allowing organizations to function efficiently.
Risk management is not a static endeavor but a continuous cycle of identification, evaluation, and adjustment. The certification underscores the importance of aligning security measures with organizational missions, ensuring that protective steps do not create roadblocks but instead harmonize with business objectives. This approach reshapes security from being perceived as a hindrance to being recognized as an enabler of trust and confidence. It is through this shift in perspective that risk-centered thinking becomes not just a professional requirement but a transformative philosophy.
The integration of risk considerations into decision-making ensures that leaders are not blindsided by unanticipated vulnerabilities. By adopting structured frameworks, organizations can identify their weak points before adversaries exploit them. For the professional pursuing the credential, this discipline instills the practice of systematically approaching challenges, rather than reacting with haste or uncertainty. Ultimately, the significance of risk-centered thinking extends beyond passing an examination and seeps into the way professionals analyze, respond, and lead within their respective environments.
The Interconnected Domains of Mastery
The Certified Authorization Professional credential rests upon seven interconnected domains of knowledge, each designed to address a specific segment of risk and authorization management. These domains are not isolated silos but threads that weave into a cohesive whole. Mastery of one domain enhances understanding of the others, reinforcing the holistic nature of the certification.
The first of these involves categorizing information systems in a manner that clarifies the potential impact of compromise. Without categorization, protective measures may either be excessive or insufficient, leaving systems vulnerable or burdened. From this foundation emerges the process of selecting appropriate security controls. These controls, chosen in relation to the categorization, represent the practical measures that defend against identified risks.
Assessment follows as a critical function. It is not enough to simply choose controls; they must be examined, tested, and validated for effectiveness. Professionals within this domain become evaluators, capable of scrutinizing whether safeguards truly deliver the protection they claim. The authorization process then takes center stage, demanding judgment in determining whether systems should proceed with operations or remain restricted until risks are properly addressed.
The cycle does not conclude there. Continuous monitoring sustains the vigilance required in today’s volatile environment. This domain embodies the principle that security is not a singular act but a persistent duty. Each of these domains reinforces the others, creating a network of expertise that ensures resilience. For the Certified Authorization Professional, mastery across all seven domains equips them with both breadth and depth, making them indispensable guardians of digital integrity.
The Human Element in Authorization
While the certification emphasizes frameworks and technical processes, it also acknowledges the irreplaceable role of the human element. Policies, procedures, and controls exist as lifeless artifacts until enacted by individuals who bring understanding, discernment, and ethical responsibility to the forefront. The Certified Authorization Professional is not merely a technician executing checklists but a leader capable of guiding organizations through complex decisions where risk and mission objectives converge.
The human element introduces perspective. Every decision regarding system authorization requires judgment that cannot be replicated by algorithms alone. For instance, determining whether a system’s risk is acceptable often involves weighing organizational tolerance, mission-critical needs, and the consequences of potential compromise. This requires wisdom, foresight, and at times, moral courage.
Furthermore, communication stands as a cornerstone of the human role. Risk information must be translated into a language comprehensible to executives, policymakers, and stakeholders. The Certified Authorization Professional bridges the gap between technical intricacies and strategic decisions, ensuring that security is not confined to technical teams but woven into the consciousness of the entire organization. This role elevates the professional from being a guardian of systems to becoming a cultivator of security culture, shaping how teams perceive and prioritize protection.
The Global Recognition of the Credential
Recognition is a defining strength of the Certified Authorization Professional certification. Because it adheres to rigorous international standards, it carries a weight that transcends borders and industries. This universality makes it a versatile credential, opening doors for professionals whether they aspire to work in government agencies, multinational corporations, or specialized sectors such as healthcare and finance.
The global recognition reflects a larger truth about cybersecurity itself: threats know no boundaries. A vulnerability in one region can quickly escalate into an international crisis. In this environment, professionals equipped with globally respected credentials can step into roles of responsibility with confidence. Their expertise is not confined to a single jurisdiction but instead resonates across industries that share the common challenge of safeguarding digital ecosystems.
Employers value this credential not only for its technical rigor but for its assurance of professional competence. By requiring documented experience in addition to passing the examination, it guarantees that certified individuals have demonstrated their abilities in real-world contexts. This blend of theoretical understanding and practical expertise is what makes the certification globally respected and widely sought.
The Transformational Impact on Careers
For individuals, the journey toward the Certified Authorization Professional credential represents more than a milestone; it is a catalyst for transformation. Achieving the certification enhances career trajectories by distinguishing professionals in an increasingly competitive market. With organizations placing heightened emphasis on risk management and compliance, certified individuals emerge as trusted authorities capable of shaping security strategies at the highest levels.
The impact on careers extends beyond recognition and employability. It cultivates self-confidence, as professionals know they possess the knowledge and skill set to navigate complex environments. This confidence empowers them to step into leadership positions, guiding teams and influencing organizational directions with authority. Financial rewards often accompany this progression, as employers recognize the value of retaining certified professionals who can safeguard mission-critical systems and ensure compliance with stringent standards.
Beyond the tangible rewards lies the intangible transformation of identity. Professionals who earn this credential become part of a distinguished community defined by shared values of diligence, vigilance, and commitment. This identity extends into their daily practices, shaping the way they perceive challenges and reinforcing their dedication to maintaining the highest standards of security.
The Role of Continuous Learning
A distinguishing feature of the Certified Authorization Professional journey is its insistence on continuous learning. Achieving the credential is not an endpoint but the beginning of an enduring commitment to staying informed. As threats evolve and technology advances, professionals must update their knowledge, refresh their skills, and adapt their strategies.
Continuous learning ensures that professionals remain relevant in a landscape where yesterday’s solutions may no longer suffice. This requires engagement with new frameworks, analysis of emerging threats, and participation in communities where knowledge is shared and refined. The certification serves as a reminder that expertise is not static but dynamic, shaped by dedication to growth.
Equally important, continuous learning reinforces humility. No professional, regardless of their credentials, can claim complete mastery in an ever-shifting field. The willingness to learn, unlearn, and relearn becomes as valuable as technical knowledge itself. For those holding the certification, this humility ensures they remain receptive to innovation, collaboration, and the evolving demands of global security.
The Custodianship of Organizational Trust
At its core, the Certified Authorization Professional embodies the custodianship of organizational trust. Trust is the unseen foundation upon which digital interactions are built, and without it, systems crumble. By managing risks, authorizing systems responsibly, and ensuring continuous vigilance, these professionals safeguard the trust that allows organizations to operate, innovate, and serve.
Trust is not an abstract ideal but a tangible asset. Customers, partners, and stakeholders place their confidence in organizations that demonstrate security maturity. The Certified Authorization Professional becomes a steward of this confidence, ensuring that every authorization decision reinforces reliability. This custodianship extends beyond the technical realm, shaping organizational reputation, resilience, and the ability to thrive in a world defined by uncertainty.
Through this role, the professional’s impact becomes both visible and invisible. Systems remain operational, breaches are prevented, and compliance is maintained, often without recognition of the effort required. Yet behind the scenes, their vigilance sustains the very fabric of digital society. In embracing this responsibility, the Certified Authorization Professional not only advances their own career but also contributes to a broader vision of stability and trust across interconnected networks.
The Essence of Risk Management in the CAP Framework
Risk management stands as the beating heart of the Certified Authorization Professional framework. Without its presence, the architecture of the program dissolves into fragility, leaving no foundation upon which to build trust, continuity, or strategic assurance. To master this discipline is not merely to learn a procedural checklist, but to internalize an evolving philosophy where foresight, analysis, and resilience converge. Within this framework, risk is neither viewed as an obstacle to be eliminated nor a phantom to be ignored, but as an omnipresent element that demands respect, vigilance, and balance.
Every aspect of the CAP certification rests upon the recognition that threats are inevitable, vulnerabilities are persistent, and no environment, no matter how fortified, can ever be completely immune. Rather than chasing the illusion of total safety, the CAP-certified professional embraces a more pragmatic goal: aligning risks with an organization’s tolerance, while enabling its mission to thrive. The discipline moves beyond static security to embrace dynamic equilibrium, weaving defense into the very fabric of organizational life.
This approach distinguishes those who hold the credential from those who simply practice surface-level security. The CAP professional perceives interconnections, anticipates cascading effects, and identifies patterns invisible to the untrained observer. By adopting such a mindset, risk ceases to be a lurking adversary and instead becomes a catalyst for strategic foresight, ensuring continuity of operations even under duress.
Identifying and Evaluating Threats with Precision
The first commandment of effective risk management is identification. This stage requires a meticulous gaze, attuned not only to the obvious vulnerabilities but also to subtle cracks that may widen under pressure. Within a digital ecosystem, threats rarely announce themselves boldly. They dwell quietly in overlooked patches, outdated libraries, misconfigured permissions, or even in the behavioral lapses of staff members unaware of the implications of their actions.
To identify risks under the CAP framework, one must think both technically and contextually. The Certified Authorization Professional understands that a misaligned access control list may not only open a path to unauthorized data but may also conflict with regulatory mandates, inviting financial penalties and reputational scars. Such recognition demands a panoramic awareness, spanning from micro-level configurations to macro-level organizational objectives.
Evaluation forms the natural continuation of identification. Here, the CAP professional engages in a dual consideration: likelihood and impact. Likelihood reflects the probability of exploitation, while impact embodies the severity of consequences should the risk manifest. A minor flaw in a rarely used subsystem may carry low urgency, while a small oversight in identity management could expose the entire architecture to catastrophic compromise. Through careful evaluation, the professional avoids overreaction to trivial matters and neglect of looming threats, balancing vigilance with pragmatism.
This evaluative lens also accounts for convergence. Risks rarely exist in isolation; they often amplify each other when combined. A system with outdated firmware, weak passwords, and poor monitoring does not merely face three separate risks—it faces an entangled network of vulnerabilities that multiply their collective potency. Recognizing these interactions demonstrates mastery and sets the CAP professional apart as a strategist rather than a mere technician.
Crafting Risk Mitigation Strategies That Endure
Once risks are identified and evaluated, the challenge turns toward mitigation. The Certified Authorization Professional does not chase the illusion of total elimination, for such a pursuit is doomed. Instead, the goal is to reduce exposure to levels aligned with organizational tolerance, recognizing that risk can be managed, redirected, and absorbed without dismantling the ability to function.
Mitigation manifests in diverse forms, each suited to different environments. Some organizations require technical fortification: encryption layers, intrusion detection, segmentation of networks, and hardened authentication systems. Others may benefit from refined governance: policy updates, procedural adjustments, or the cultivation of awareness through staff training. Still others demand structural change: rethinking business processes or outsourcing certain functions to partners better equipped to manage specialized risks.
The CAP-certified professional navigates this landscape with adaptability. They tailor solutions not as rigid formulas but as carefully aligned responses, harmonizing security with mission imperatives. A university cannot afford the same rigid restrictions as a defense contractor, and a healthcare system requires different safeguards than a financial institution. Recognizing these nuances, the professional ensures that mitigation measures are not only effective but sustainable, woven into the living rhythms of the organization rather than imposed as external burdens.
Equally crucial is the recognition that mitigation is a continuous process. Controls must evolve as threats evolve. A firewall rule that sufficed yesterday may prove obsolete tomorrow. Training sessions must be repeated, updated, and reinforced as technologies shift and adversaries innovate. The CAP credential signals an individual’s readiness to shepherd this ongoing process, keeping defenses agile without succumbing to fatigue or complacency.
The Imperative of Risk Communication
No matter how refined, risk management cannot flourish in silence. Communication stands as its lifeline, bridging the technical realm with the strategic vision of leadership and the operational realities of users. A Certified Authorization Professional must become a translator, converting intricate technical assessments into language that resonates with stakeholders across the organizational hierarchy.
Executives do not require an overload of acronyms or configuration details; they require clarity on potential impacts to revenue, reputation, and continuity. End-users do not need complex diagrams of threat vectors; they need clear guidance on behaviors that preserve security without hindering productivity. Regulators seek documented assurance that practices align with compliance requirements, while partners demand evidence that shared data remains safeguarded.
The professional who excels in risk communication ensures that security is not perceived as a barrier but as an enabler. When leadership understands that risk-aligned decisions protect strategic growth, investments in security become not grudging concessions but deliberate priorities. When staff comprehend how their daily practices shape resilience, they shift from reluctant participants to empowered allies. This cultural shift, cultivated through precise and empathetic communication, multiplies the effectiveness of every safeguard, embedding risk awareness into the collective consciousness of the organization.
Continuous Monitoring and the Evolution of Risk
Risk does not stand still. It flows, shifts, mutates, and evolves in tandem with technological progress and adversarial innovation. A system deemed secure today may become vulnerable within weeks as new exploits emerge, configurations drift, or staff turnover introduces unfamiliarity. To address this reality, the Certified Authorization Professional embraces continuous monitoring as an indispensable component of risk management.
Continuous monitoring extends beyond the mere deployment of tools. It requires a vigilant ecosystem where logs are scrutinized, anomalies investigated, and patterns discerned. The CAP-certified individual interprets signals from intrusion detection systems, correlates them with contextual data, and translates them into actionable insights. Yet the effort is not purely technical—it is strategic, ensuring that risk assessments remain current and that mitigation measures remain aligned with organizational objectives.
Through continuous engagement, the professional ensures that resilience is not episodic but perpetual. Controls are adjusted not only after breaches but in anticipation of emerging threats. Policies evolve alongside industry trends. Training adapts to new user behaviors. This rhythm transforms security from a reactive posture into a proactive commitment, one that anticipates shocks rather than merely enduring them.
The CAP framework teaches that continuity of monitoring also strengthens accountability. Documentation of observations, responses, and decisions provides verifiable proof of diligence, satisfying compliance demands and reinforcing organizational credibility. In this way, monitoring becomes not a tedious obligation but a living testament to vigilance and discipline.
Organizational and Professional Transformation Through Risk Management
Embedding risk management within the daily operations of an organization delivers profound transformation. At the institutional level, it fosters resilience, enabling systems to absorb disruptions without collapsing. A breach that might devastate an unprepared enterprise becomes a recoverable incident for one guided by CAP-certified professionals. Preparedness becomes not a reactive scramble but a proactive shield, reducing both probability and severity of harm.
The organizational benefits extend to reputation and trust. Partners, clients, and customers gain confidence in entities that demonstrate clear, consistent risk management. Financial stakeholders recognize the reduced likelihood of costly incidents. Regulators view compliance not as grudgingly achieved but as seamlessly integrated. The cultural tone shifts, transforming security from a grudging expense into a strategic advantage.
For individuals, the rewards are equally profound. Mastery of risk management through the CAP credential positions professionals as more than technical specialists. They emerge as trusted advisors, strategic thinkers, and leaders capable of guiding organizations through uncertainty. This credibility opens doors to roles of greater responsibility, where vision and execution converge. The professional identity evolves, grounded in both expertise and foresight, setting them apart in a competitive field.
The interplay of organizational resilience and professional recognition creates a virtuous cycle. As professionals grow in stature, organizations grow in strength. As organizations demonstrate resilience, professionals gain greater opportunities to influence. Within this cycle, the Certified Authorization Professional becomes both guardian and architect, shaping not only defenses but futures.
Governance of Enterprise IT
The structure of governance within enterprise IT forms the cornerstone of the Certified Authorization Professional framework. This domain does not stand as a rigid wall of directives, but rather as a living foundation that ensures information systems align harmoniously with the overarching mission of an organization. Governance is a deliberate weaving of vision, accountability, and operational clarity. It exists not to impose barriers, but to create guiding channels through which security objectives flow effortlessly.
When governance is sound, it establishes a culture of responsibility. Policies and procedures become more than documents; they evolve into living instruments that inspire confidence and strengthen organizational resilience. Governance ensures that systems are not simply managed but stewarded with foresight. It interlaces the aspirations of leadership with the tangible mechanisms of protection. In this way, governance functions as both compass and anchor, providing strategic orientation while stabilizing the complex architecture of information systems.
Within this realm, the Certified Authorization Professional becomes a custodian of balance, ensuring that corporate ambitions do not drift away from necessary safeguards. Governance teaches the art of harmonizing ambition with prudence, charting a course where organizational goals are never pursued at the expense of trust and reliability. It is here that the seeds of effective authorization are sown, for without governance, the remaining domains lack the structure upon which to flourish.
Risk Management
Risk management occupies the second domain and represents the ever-present heartbeat of the certification. Unlike governance, which establishes the framework, risk management thrives in the dynamic motion of discovery, assessment, and mitigation. It is a discipline of foresight, constantly looking ahead to identify where vulnerabilities might emerge and where adversaries may attempt to intrude.
The essence of risk management lies not in fear but in readiness. It teaches that uncertainty can never be erased but must be embraced, studied, and shaped into manageable forms. Through careful analysis, risks are categorized, prioritized, and addressed with precision. This process transforms what might seem overwhelming into structured action. The Certified Authorization Professional must not only recognize threats but also weigh their impact against organizational values, resources, and long-term goals.
Resilience emerges as the crowning reward of risk management. An enterprise that practices it faithfully does not stumble blindly into challenges but strides forward with adaptability. The interconnection of strategy and execution becomes evident, for choices made in the boardroom echo through technical implementations, while actions in the data center reflect on business continuity. Risk management weaves these layers together, ensuring that no decision is isolated and no safeguard stands detached from the wider landscape.
Information Systems Acquisition
The acquisition of information systems, the third domain, underscores the truth that security must be cultivated at the earliest stage. Whether solutions are forged internally or procured from outside vendors, the moment of acquisition is the moment when future stability is decided. To neglect security in these initial phases is to plant seeds of weakness that may later grow into costly vulnerabilities.
This domain requires professionals to serve as vigilant evaluators, ensuring that procurement is not guided solely by performance or price but also by the invisible threads of protection. Security requirements must be interwoven into contracts, specifications, and expectations. Acquisition is not a transaction of technology alone but a transfer of responsibility, where oversight ensures that every new system enters the organization already prepared for its role in a protected environment.
The Certified Authorization Professional approaches acquisition as both analyst and guardian. Technical compatibility is scrutinized alongside long-term resilience, and each chosen system becomes part of a tapestry where every element strengthens the whole. By embedding safeguards from the outset, acquisition transforms from a mere logistical task into an act of strategic foresight. This ensures that systems are born not with fragility but with endurance, ready to evolve securely as organizational needs shift.
Development and Maintenance
Development and maintenance extend the continuum of protection throughout the operational lifespan of systems. Information systems, by their nature, are living entities that evolve with every patch, upgrade, and modification. Each adjustment, while designed to improve, also introduces potential risks. The Certified Authorization Professional stands guard over these changes, ensuring that vigilance is never abandoned in the name of convenience.
Maintenance is not a monotonous ritual of updates but a dynamic practice of preservation. Every new feature, every corrected flaw, must be examined through the lens of security. The unseen threads of integrity must remain unbroken, even as layers are added and functions evolve. The domain insists upon patience, precision, and unwavering scrutiny.
Through this lens, development ceases to be an isolated act of innovation. It becomes an integrated dialogue between creativity and caution, where ideas are refined by the enduring demand for trustworthiness. Maintenance, in turn, acts as the watchful steward, preserving the strength of these creations against the relentless tide of threats. Together, development and maintenance form the cycle that ensures systems remain as resilient tomorrow as they were at the moment of inception.
Operations and Maintenance
The fifth domain brings attention to the rhythm of daily activity, where security is lived rather than merely planned. Operations and maintenance are the pulse of the information environment, ensuring that controls are not dormant rules but active guardians. Within this domain, the Certified Authorization Professional nurtures a state of constant attentiveness, where access rights are regulated, systems are monitored, and anomalies are pursued with resolve.
Day-to-day operations demand discipline, a willingness to engage with the ordinary tasks that safeguard extraordinary value. From the careful assignment of user privileges to the persistent observation of logs and alerts, every small action builds toward a climate of trust. Maintenance here not only preserves technology but also sustains human confidence in the system.
What distinguishes excellence in this domain is the ability to treat routine duties not as burdens but as the quiet acts of vigilance that form the backbone of resilience. Operations remind us that security is not a distant event but a present practice. It is in the unbroken repetition of detail, the steady oversight of function, that enterprises remain fortified against disruption.
Disposal of Systems
The lifecycle of information systems concludes with disposal, the sixth domain. Too often overlooked, this stage is as critical as the birth of a system. Without secure disposal, remnants of data may remain vulnerable, offering adversaries an unexpected doorway into organizational memory. Disposal transforms the ending of a system’s journey into an act of protection, ensuring that what once served faithfully does not become a liability.
Secure disposal may involve wiping, destruction, or carefully planned archiving, each method chosen with an eye toward the sensitivity of the data involved. What defines this domain is not the technique but the intent: to leave no fragment behind that could compromise the integrity of the enterprise. The Certified Authorization Professional assumes the role of a final custodian, ensuring that closure is as secure as inception.
This process also symbolizes respect for the information once entrusted to the system. By ensuring secure disposal, professionals affirm their commitment to confidentiality, integrity, and trustworthiness, even in the final stage of a system’s life. Disposal, then, is not an afterthought but a deliberate act of closure, sealing the lifecycle with dignity and vigilance.
Assessment and Authorization
The seventh domain unites the preceding elements into a cohesive framework. Assessment and authorization represent the moment when preparation, governance, risk management, acquisition, development, operations, and disposal converge into judgment. This domain demands both technical precision and managerial discernment, as systems are evaluated to determine whether they may be entrusted with operational responsibility.
Assessment is the act of measuring the strength of implemented controls, weighing them against the standards of resilience demanded by the organization. Authorization follows as a decision rooted in evidence, documentation, and accountability. The Certified Authorization Professional becomes both evaluator and decision-maker, bridging the gap between technical assurance and organizational leadership.
This domain exemplifies the fusion of people, processes, and technology. It underscores that authorization is not a mechanical approval but a thoughtful confirmation that every safeguard is aligned and every risk understood. The process strengthens trust, assuring that systems are not merely functional but fortified against disruption.
Assessment and authorization represent the culmination of vigilance, where all domains converge into action. It is in this final stage that the holistic nature of the certification becomes clear, for no single element stands alone. Instead, every layer contributes to the assurance that systems operate with integrity, resilience, and foresight.
Understanding the Path of Preparation
Preparing for the Certified Authorization Professional exam is an intricate journey that demands both intellectual discipline and steady perseverance. This is not an endeavor that rewards quick shortcuts, but one that honors deep comprehension and consistent practice. The exam is designed to evaluate how candidates think, apply frameworks, and handle complexities under pressure. With 125 multiple-choice questions to be tackled within three hours, the assessment calls for knowledge, endurance, and methodical time management. The scope of preparation extends well beyond simply reading materials. It involves weaving together theory, practice, and reflection into a balanced approach. Candidates who commit to this path find themselves not only ready for the test but also more adept in real-world cybersecurity challenges.
The exam evaluates a candidate’s grasp of the Risk Management Framework, a methodology that emphasizes ongoing assessment, authorization, and monitoring. Understanding its nuances requires both study and experience. Those preparing must internalize how the framework unfolds across different stages, from categorization to continuous monitoring. Each stage presents a web of requirements, roles, and responsibilities, and the exam seeks to confirm that the candidate can apply them holistically rather than in isolation.
The Role of Structured Study
Structured study is the backbone of exam readiness. Without a clear plan, the overwhelming breadth of material can easily lead to disarray. Candidates benefit from segmenting their learning into manageable sessions, aligning their study with the seven key domains that the exam encompasses. Each domain unfolds a different perspective of risk management, whether related to security controls, documentation, or authorization processes. By steadily focusing on one area at a time, learners absorb the material more thoroughly.
Practice exams play an indispensable role in this structured approach. They introduce candidates to the rhythm of questions, the subtle phrasing, and the traps embedded within multiple-choice formats. By reviewing results critically, learners uncover their weak areas and recalibrate their study. This practice transforms anxiety into familiarity, reducing surprises on the actual day.
Yet, study is not only about books or practice questions. It also involves reflection. When candidates pause after each session to consider how a concept might apply in a real scenario, they strengthen their long-term memory. In this way, theoretical points stop being abstract and instead become part of a practical skillset that supports both exam success and professional practice.
Harnessing the Power of Practical Experience
Practical exposure is often the defining factor between candidates who merely pass and those who excel. Risk management and system authorization are not academic constructs but living practices shaped by organizational demands, regulatory requirements, and technological shifts. When individuals engage with these concepts directly in their professional environments, they build insights that cannot be fully captured through theory alone.
For those already immersed in cybersecurity roles, preparation becomes an exercise in connecting daily responsibilities with the exam domains. Every policy written, every system authorization completed, and every control evaluated contributes to a deeper familiarity. This kind of exposure ensures that when a scenario-based question appears on the test, the candidate recalls more than a definition—they remember an actual challenge they once encountered.
Those who lack such direct experience must find creative ways to build it. Internships, mentorship programs, and volunteer opportunities provide valuable exposure. Even shadowing a professional in a risk management role offers glimpses into how decisions unfold in practice. These opportunities, combined with theoretical study, build a balanced readiness that aligns with the spirit of the exam.
Cultivating Mental Endurance
Three hours may seem manageable at first glance, but in the high-stakes environment of a certification exam, it can become daunting. Mental endurance is as vital as intellectual preparation. Candidates must train themselves to remain attentive, composed, and confident throughout the entire duration. Timed practice tests serve as one of the best tools for developing this stamina. By simulating the real environment, learners build the focus necessary to sustain accuracy without fatigue.
Equally important are strategies for managing stress. Simple techniques such as controlled breathing, mindfulness exercises, or short mental resets during practice can make a noticeable difference. On exam day, these methods prevent panic and help restore clarity when the mind begins to wander or stumble. Confidence is built not only on knowing the content but also on trusting one’s ability to remain calm under pressure.
Endurance also involves maintaining balance in the days leading up to the exam. Adequate rest, healthy nourishment, and a steady rhythm of study and breaks cultivate an alert and receptive state of mind. Candidates who exhaust themselves with last-minute cramming often find their focus unraveling under timed conditions. In contrast, those who approach the day with equilibrium are better equipped to navigate its demands.
Balancing Knowledge Across All Domains
Success in the Certified Authorization Professional exam is not measured by excelling in only one domain. The scoring system requires candidates to achieve consistent competence across the full spectrum. A passing score of 700 out of 1000 underscores the principle that a broad and balanced understanding is essential. This reflects the professional reality, where an authorization expert must integrate perspectives from multiple areas rather than relying solely on niche expertise.
Balanced preparation means resisting the temptation to neglect weaker areas in favor of stronger ones. Instead, candidates must devote extra attention to those domains that feel less intuitive. Study sessions should be distributed with care, ensuring that no part of the framework is overlooked. Even if certain areas appear minor, every question carries weight, and gaps in knowledge can accumulate quickly.
This holistic focus also mirrors the broader philosophy of risk management itself, which emphasizes that no component exists in isolation. Security is only as strong as its weakest element, and comprehensive knowledge ensures that professionals can identify, address, and manage risks from all angles.
Lifelong Commitment Beyond the Exam
Passing the Certified Authorization Professional exam is a milestone, but it does not mark the end of learning. The certification demands continuous professional education, requiring candidates to earn credits that demonstrate ongoing development. This ensures that credential holders remain aligned with evolving threats, new technologies, and emerging best practices.
The requirement for continuing education underscores a deeper truth: cybersecurity is not static. Systems evolve, attackers adapt, and regulatory landscapes shift constantly. Professionals must remain vigilant, not only to preserve their certification but also to safeguard the organizations and communities they serve.
This lifelong learning ethos transforms the exam from a one-time hurdle into part of a larger journey. Those who embrace it find that preparation for the test was only the beginning of a rewarding path of growth, refinement, and contribution. Every seminar attended, every project completed, every new method explored adds to their repertoire of skills, strengthening their role as trusted experts.
Transformative Power of the Journey
Preparation for the Certified Authorization Professional exam is more than a technical challenge. It is a transformative process that reshapes the candidate’s perspective and capabilities. The long hours of study cultivate discipline, while the hands-on experiences sharpen judgment. The endurance training strengthens resilience, and the balanced approach fosters adaptability. Together, these elements create not only a successful candidate but also a more competent professional ready to confront the complexities of modern cybersecurity.
This transformation is the true reward. While the passing score validates readiness, it is the journey itself that forges expertise. Candidates who immerse themselves fully emerge with more than a certificate. They gain confidence, clarity, and a refined ability to navigate the intricate interplay of technology, regulation, and risk. Their preparation echoes in their daily practice, equipping them to contribute meaningfully to their field long after the exam day has passed.
Industry Recognition and the Emergence of Certified Authorization Professional
The Certified Authorization Professional certification stands as a mark of authority in the evolving sphere of risk management and information protection. It embodies not only technical ability but also the maturity to interpret and implement structured frameworks that protect the lifeblood of modern organizations—data. In contemporary times, where threats manifest in increasingly sophisticated forms, the recognition of such certification stretches beyond borders. Industries spanning finance, government, health, energy, and defense observe it as a credible assurance of expertise. Employers seek individuals who can align security initiatives with broader business visions, and this credential becomes the bridge between governance and innovation.
Global acknowledgment of the certification is reinforced by its compliance with international benchmarks. By conforming to rigorous evaluation criteria, it assures stakeholders that certified professionals carry a validated skill set. This stature resonates with employers, auditors, regulators, and peers alike, strengthening the professional identity of those who attain it. The credential evolves into more than a line on a résumé; it is an emblem of trust in an unpredictable digital landscape.
The Value of Structured Risk Management
Risk management forms the backbone of every enterprise that depends on information technology, which is to say, nearly all modern organizations. The Certified Authorization Professional framework emphasizes a cycle of identifying, evaluating, mitigating, and monitoring risks. This approach is neither theoretical nor stagnant; it adapts fluidly to the ever-changing threat environment. Whether it involves insider risks, supply chain vulnerabilities, or cloud-based exposures, the methodology remains steadfast in guiding professionals toward resilience.
The structured nature of the certification ensures that its holders not only comprehend threats but also know how to position defenses in a manner that strengthens the organization’s overall mission. The recognition of these capabilities by leaders, auditors, and industry authorities creates an environment where certified professionals serve as vital intermediaries. They interpret the technical domain for decision-makers and, conversely, translate strategic goals into actionable security measures. Such dual fluency makes them indispensable across industries.
Expanding Professional Horizons
For individuals who achieve the Certified Authorization Professional designation, the benefits extend well beyond knowledge validation. The credential amplifies professional opportunities, equipping individuals to pursue career mobility across regions and industries. Its presence on a professional profile signals readiness for elevated responsibilities such as risk governance, compliance oversight, or leadership within cybersecurity divisions.
The expansion of digital ecosystems creates a persistent demand for professionals who can safeguard interconnected systems while maintaining organizational agility. Those certified under this framework find themselves well-positioned to assume advisory roles, guiding enterprises through turbulent digital environments. The credential not only enhances earning potential but also grants its holders the reputation of being adaptable, resilient, and prepared to tackle unforeseen challenges. In essence, it is a launchpad toward more advanced professional pursuits.
The Global Stature of the Credential
Recognition of the Certified Authorization Professional certification continues to increase in both public and private sectors. As enterprises embrace digital transformation, they require professionals who can assure stakeholders that sensitive data, operational continuity, and compliance obligations are secure. The certification’s alignment with international frameworks and its validation under strict accreditation standards magnify its global stature.
Employers across continents interpret the certification as evidence of both technical fluency and governance-oriented judgment. It distinguishes certified individuals from the larger workforce by symbolizing a blend of technical precision and strategic foresight. This duality is critical in environments where technology and regulation evolve in parallel, and organizations must maintain trust with their clients, partners, and regulators.
The Ever-Changing Threat Landscape
Digital adversaries evolve constantly, exploiting new technologies and complex networks. This shifting landscape requires organizations to adopt adaptive defense measures that remain aligned with long-term objectives. Certified Authorization Professionals are trained to approach these challenges with a steady framework that can be recalibrated as environments transform. They are not merely defenders of current systems; they are forward-looking practitioners capable of anticipating risks before they fully materialize.
As organizations expand into cloud infrastructures, artificial intelligence applications, and interconnected supply chains, the complexity of security obligations grows. Certified professionals are equipped to navigate these intricacies with confidence, ensuring that governance, compliance, and security practices remain consistent amid transformation. Their role does not diminish with automation or advanced technology; instead, it expands to include oversight, interpretation, and strategic alignment.
Pathways Toward Leadership and Specialization
For many professionals, achieving the Certified Authorization Professional credential becomes a gateway to leadership roles. The knowledge base and credibility established through certification prepare individuals to assume positions such as Chief Information Security Officer, Director of Risk Management, or head of compliance divisions. These roles demand more than technical expertise; they require vision, communication skills, and the ability to harmonize security initiatives with organizational ambitions.
Others may channel their certification toward specialization, choosing to focus on areas such as incident response, regulatory compliance, or emerging domains like cloud and artificial intelligence security. The flexibility of the credential lies in its foundational principles, which remain relevant regardless of technological shifts. As industries grow and new challenges appear, certified professionals find themselves capable of evolving alongside the digital landscape, carving distinct pathways that suit their aspirations.
The Enduring Relevance of Certified Authorization Professionals
While technologies, tools, and infrastructures inevitably evolve, the principles underpinning risk management and system authorization remain timeless. Certified Authorization Professionals carry with them a methodology that transcends fleeting trends. Their recognition stems not only from current achievements but also from their ability to sustain relevance in uncertain futures.
This endurance assures organizations that certified individuals are not bound to specific tools or temporary fashions but are instead rooted in enduring strategies. The certification establishes them as guardians of stability in a world where instability is the norm. For professionals themselves, it ensures that their skills, credibility, and influence grow in tandem with the industries they serve, making the Certified Authorization Professional credential a cornerstone of both personal and organizational resilience.
Conclusion
The Certified Authorization Professional certification stands as one of the most valuable credentials for individuals seeking to excel in risk management, information assurance, and system authorization. Rooted in the principles of the Risk Management Framework, it is far more than a technical qualification; it represents a structured way of thinking about uncertainty, resilience, and organizational trust. By validating the ability to assess, categorize, implement, and monitor security measures, the certification ensures that professionals can translate policy into protection and theory into practical safeguards.
For individuals, achieving this certification unlocks expanded career opportunities, enhanced credibility, and recognition as a trusted authority in the field. It signals mastery of both strategy and detail, enabling professionals to guide organizations through complex security challenges with clarity and confidence. For organizations, employing CAP-certified experts strengthens defenses against evolving threats, ensures compliance with global standards, and supports a culture of proactive risk management.
What makes this certification enduringly relevant is its balance between technical rigor and strategic vision. It reinforces the idea that security is not a one-time achievement but an ongoing commitment to vigilance and adaptation. As digital systems become increasingly interconnected and adversaries grow more sophisticated, the need for structured frameworks and skilled professionals will only intensify.
The CAP credential is therefore not just a milestone but a pathway. It empowers professionals to grow, adapt, and lead in a world where information is both the greatest asset and the most vulnerable target. By embracing the principles it upholds, Certified Authorization Professionals help create organizations that are not fragile in the face of risk but resilient, agile, and trustworthy. In an age where security is synonymous with survival, their role is indispensable—and their impact far-reaching.
Top ISC Exams
- CISSP - Certified Information Systems Security Professional
- CCSP - Certified Cloud Security Professional (CCSP)
- SSCP - System Security Certified Practitioner (SSCP)
- CISSP-ISSAP - Information Systems Security Architecture Professional
- CISSP-ISSMP - Information Systems Security Management Professional
- CAP - Certified Authorization Professional
- CSSLP - Certified Secure Software Lifecycle Professional
- CISSP-ISSEP - Information Systems Security Engineering Professional