Certification: CAP
Certification Full Name: Certified Authorization Professional
Certification Provider: ISC
Exam Code: CAP
Exam Name: Certified Authorization Professional
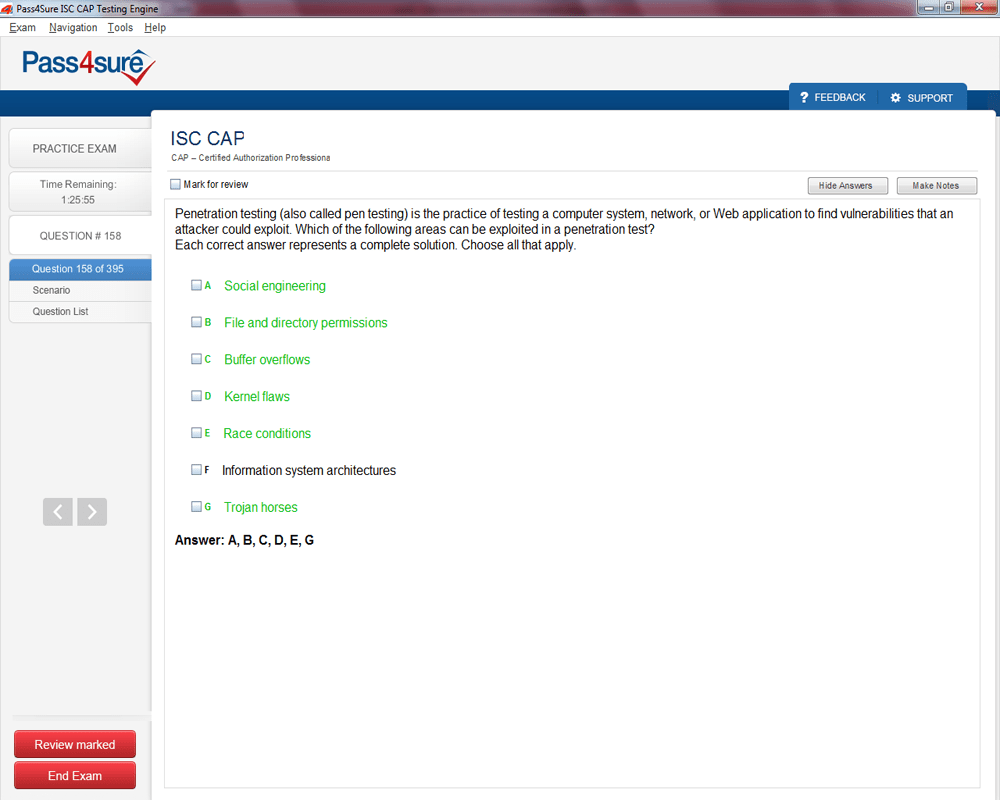
CAP Exam Product Screenshots
CAP Product Reviews
My dream came true
"I am just writing to say thank you for helping me to pass my CAP Certifications exam. I had previously failed my first attempt to pass the ISC exam in 2009 and since then have been afraid to take the new CAP Certifications exam for fear of failing a second time. After going through another study course twice in the last two years, I needed a change and a new approach. It was just the thing I needed. While the other study course was very thorough, I needed the simplicity that your course offered and I passed with 30 points to spare! Thank you again for helping me to achieve my dream!
Sincerely,
Mary Jane Walker"
pass 4 sure is amazing
"I recently found out I passed all four sections of the CAP Certifications exam exam and I owe it all to pass 4 sure. I recently found out I passed all four sections of the ISC exam and I owe it all to pass 4 sure. For the past 15 months, I have taken and retaken sections multiple times. So much so that I really thought about quitting, but perseverance and the unwillingness to give up kept me going. People who pass the CAP Certifications exam test are not the smartest. It is those that stick it to the end. And I am so glad I am one of them!
Joseph Chen"
I was able to go back and contribute due to pass 4 sure!
"I was able to go back and contribute to my country thanks to the great assistance from pass 4 sure CAP Certifications exam prep class.I am very surprised to see that I achieve a mile stone in my life. I was able to go back and contribute to my country thanks to the great assistance from pass 4 sure class. I was able to pass the CAP Certifications exam test on my second trial after a care ful follow through of the methods mentioned in the pass 4 sure class. I was able to go back and contribute to my country thanks to the great assistance from pass 4 sure class. I was able to pass the CAP Certifications exam test on my second trial after a care ful follow through of the methods mentioned in the pass 4 sure class.
Viga Dura Borge"
My Sincere gratitude to Pass4sure Team
"I just took the CAP Certifications exam and passed last week. Thank you for your wonderful study guide for the preparation of this tough ISC exam. I don't think I would have passed CAP Certifications without it. I carefully read all the preparation instructions and followed them truly and this is the only reason for my success. You really helped me not be too nervous for the test, and I actually enjoyed studying for it!
Thank you.
Andrea Euser"
It was a brilliant success
"I took CAP Certifications exam and received my results, it was a brilliant success. ISC exam material was my only source of study. And PASS4SURE did greatly, I felt so much prepared and confident after learning from your material. I have been recommending CAP Certifications exam material to my companions preparing for this paper. Thanks!
Terry"
I have got a treasure and that is Pass4sure
"Hey Pass4sure
For me pass4sure is simply more than a treasure because I was a hopeless case in studies and it was unthinkable for me to appear and pass CAP Certifications cert exam in first attempt. Before appearing I was told to go through by number of test engines for the preparations of ISC cert exam but I finally selected pass4sure. My choice was right and I have made a new record of passing CAP Certifications cert exam with 92 percent this is my highest ever score , that’s why pass4sure for me you are more than a treasure. Though I am not very brilliant but with you I think I can add another certification to my credentials.
Thank you
Tim Steven"
Reason of my success!
"I passed CAP Certifications exam few months ago. The ISC exam was the toughest exam I have ever taken in my life. But the best thing is that exam was a success. I totally give credit of my success to Pass4sure’s ISC exam material, because Pass4sure material was my primary source of preparation. There is no way for complete preparation of CAP Certifications exam except Pass4sure support and help. Thanks.
Allen"
Passed single handedly with pass4sure guidance
"Hey Today
I am glad and proud to inform everyone that I have passed CAP Certifications exam with flying colors. Without the help and support of pass4sure it wasn’t possible to pass with such an ease. I prepared for CAP Certifications at home without joining an institute or wasting my time and money on boot camps. I simply downloaded the preparation material for ISC exam and prepared with it. Now I am enjoying my career and doing wonders at my workplace.
Thanks
Tyler Purdy"
So excited to tell…..
"Hi, I am so excited to tell you that I passed my CAP Certifications exam. Your material did a great job of preparing me for ISC exam. Your help and support boosted my confidence for CAP Certifications exam. I could not have done this without Pass4sure.
RAMEN"
With positive results I have gained much confidence
"Hi everyone
I took CAP Certifications exam today and unbelievingly passed in first attempt with the score of 924. I used pass4sure’s ISC study materials and believe me this product will surely get you positive results in CAP Certifications exam due to which you guys will feel a confidence in yourselves like I am feeling. Pass4sure has really improved my qualification and for that I will always be thankful.
I really owe you pass4sure and from now and onwards I will not stop recommending your products to other candidates.
Thank you so much
Tamara Stoll"
CMMC Assessment Process (CAP) Explained: Step-by-Step
In the realm of cybersecurity, organizations that handle Controlled Unclassified Information (CUI) face mounting challenges. With cyber threats becoming more sophisticated, securing sensitive data is no longer optional—it’s a necessity. The Cybersecurity Maturity Model Certification (CMMC) provides a detailed and structured framework to protect sensitive data, especially for entities collaborating with the U.S. Department of Defense (DoD). Among the various CMMC levels, Level 2 stands out as a critical milestone. It bridges the gap between basic and advanced cybersecurity practices, providing organizations with a robust methodology to safeguard their systems against potential cyberattacks. Achieving CMMC Level 2 certification offers numerous benefits, from mitigating cyber risks to enhancing organizational reputation.
Organizations seeking this certification must adhere to a defined assessment process. This process is intricate, demanding thorough preparation and a detailed understanding of cybersecurity practices. Understanding the framework behind the CMMC Level 2 assessment is fundamental for any organization aiming for certification. The assessment ensures that an organization not only complies with cybersecurity protocols but also establishes an enduring commitment to safeguarding sensitive information. This commitment is vital for fostering trust and securing valuable partnerships with government agencies, defense contractors, and other critical stakeholders.
The Initial Phase: Preparation for the CMMC Level 2 Assessment
The first stage in the journey toward CMMC Level 2 certification is all about preparation. Organizations need to understand the core components of the assessment process, ensuring that every requirement is met with precision. Preparation entails careful alignment of the organization’s security practices with the standards outlined in the CMMC framework, which are primarily based on the National Institute of Standards and Technology (NIST) SP 800-171 guidelines. These guidelines encompass security controls for handling CUI, covering areas such as access control, incident response, and system integrity.
Organizations must first ensure they have the necessary documentation and systems in place to demonstrate compliance. The preparation phase involves not only reviewing existing cybersecurity measures but also making necessary adjustments to meet the standards required for CMMC Level 2 certification. This can range from enhancing encryption protocols to implementing stronger access control mechanisms. The organization’s senior leadership must be involved in this phase, as their commitment and resources will drive the success of the entire certification process.
As part of the preparation, the organization must also engage with a CMMC Third-Party Assessment Organization (C3PAO). C3PAOs are accredited entities responsible for conducting the CMMC assessment. It’s important to note that C3PAOs are not only qualified but are also impartial, ensuring an unbiased and credible evaluation of the organization’s cybersecurity practices. This collaboration begins with initial consultations to understand the scope of the assessment and the particular systems that will be evaluated.
Defining the Scope of the CMMC Level 2 Assessment
Once the preliminary preparation has been completed, one of the most critical steps in the CMMC Level 2 assessment process is defining the scope. This step involves identifying the specific systems, processes, and assets that will be examined during the assessment. It is essential to recognize that the scope should be tailored to the needs of the organization and the type of information it handles.
For example, not all systems within an organization may need to be included in the scope. If an organization processes CUI in only certain departments or systems, the assessment may focus solely on those areas. The C3PAO will work closely with the organization to determine the boundaries of the evaluation, ensuring that all necessary systems handling CUI are covered, while excluding any irrelevant systems. This precise scoping helps optimize the assessment process, allowing the C3PAO to apply a more targeted and effective evaluation methodology.
In some instances, the organization may have undergone a self-assessment before seeking formal certification. This self-assessment helps identify any potential gaps in cybersecurity practices and provides an initial benchmark. While a self-assessment is not a requirement for CMMC Level 2 certification, it can significantly streamline the formal assessment process, as many of the preparatory activities have already been completed. The C3PAO will review the self-assessment findings and validate them as part of the overall evaluation.
Documentation: The Backbone of the CMMC Level 2 Assessment
An often overlooked yet essential element of the CMMC Level 2 assessment process is the preparation of documentation. The key document that serves as the cornerstone for the assessment is the System Security Plan (SSP). This comprehensive document provides an overview of the organization’s cybersecurity practices, detailing how it adheres to NIST SP 800-171 guidelines. It outlines the security measures in place to protect CUI and serves as evidence during the assessment process.
The SSP is a living document, constantly updated as the organization’s cybersecurity posture evolves. It should include details such as the organizational structure, specific security controls implemented, risk management strategies, and any gaps that need to be addressed. The document must also explain how the organization continuously monitors and manages cybersecurity risks to ensure compliance with CMMC Level 2 standards.
In addition to the SSP, the organization may need to provide supplementary documents that further demonstrate adherence to security standards. This could include incident response plans, access control policies, and audit logs. All documentation must be thorough, well-organized, and readily accessible to the C3PAO. Having these documents in place not only expedites the assessment process but also reinforces the organization’s commitment to maintaining a secure and compliant cybersecurity environment.
Managing Conflicts of Interest in the Assessment Process
Maintaining integrity throughout the CMMC Level 2 assessment process is crucial. One of the key factors that ensures the credibility of the evaluation is the management of conflicts of interest (COI). A conflict of interest can undermine the impartiality of the assessment and lead to skewed or unreliable results. Both the organization seeking certification (OSC) and the C3PAO must take proactive steps to identify and address any potential COIs before the assessment begins.
The C3PAO is responsible for ensuring that the individuals conducting the assessment have no vested interests in the outcome. This is particularly important as the assessment could affect the reputation and security posture of the organization undergoing evaluation. Both parties must disclose any relationships that might present a conflict, whether it’s a financial interest, previous business association, or any other factor that could influence the results.
A transparent process for identifying and addressing COIs is not only a requirement but also helps build trust in the CMMC framework. By ensuring that the evaluation is free from external influences, both the OSC and the C3PAO can work together to guarantee that the assessment results are an accurate reflection of the organization’s cybersecurity practices.
Legal and Contractual Considerations in the CMMC Level 2 Assessment
Once the preparatory steps, including scoping, documentation, and COI management, are in place, the next phase is to formalize the relationship between the organization seeking certification and the C3PAO. This is done through a contractual agreement that outlines the terms, deliverables, and expectations of both parties.
The contract is a binding document that ensures both the OSC and the C3PAO adhere to the agreed-upon schedule and responsibilities. A crucial aspect of this contract is the mutual non-disclosure agreement (NDA), which guarantees that all sensitive information shared during the assessment remains confidential. Given the nature of CUI and the potential risks associated with data breaches, this confidentiality agreement is paramount. Both parties must understand the importance of safeguarding any proprietary or classified information that may be disclosed during the assessment.
The contract also covers logistical aspects, such as the timing of the assessment, the number of personnel involved, and the specific deliverables expected from both parties. Clear terms and conditions ensure that both the OSC and the C3PAO have aligned expectations, preventing misunderstandings that could lead to delays or complications during the assessment process.
A Collaborative Approach to the CMMC Level 2 Assessment
The CMMC Level 2 assessment is not a solitary endeavor but rather a collaborative process between the OSC and the C3PAO. Both parties must work closely together to ensure that every aspect of the assessment is conducted efficiently and effectively. This cooperation is crucial for addressing any issues that arise, whether they involve documentation, scope, or technical matters.
The success of the CMMC Level 2 certification hinges on the ability of both parties to communicate openly and transparently. Regular check-ins, feedback loops, and alignment meetings are essential to maintaining the momentum of the process. While the assessment may be time-consuming and rigorous, a well-managed partnership between the OSC and the C3PAO ensures a smooth and successful evaluation.
As organizations continue to navigate the complexities of cybersecurity compliance, the CMMC framework serves as a guiding principle. Level 2 certification, in particular, offers organizations a well-defined pathway to improve their security practices while demonstrating a commitment to the protection of sensitive information. By understanding and following the structured assessment process, organizations can significantly enhance their cybersecurity posture and bolster their position in the competitive landscape.
The Essence of Creativity in the Modern World
Creativity, often regarded as the spark that drives innovation, has become a crucial element in every facet of life. In today’s rapidly evolving world, where technology and social norms constantly shift, creativity serves as a beacon guiding individuals and organizations through uncharted waters. It is the ability to think outside conventional boundaries and approach problems from a fresh perspective. Whether in art, business, technology, or personal development, creativity enables us to adapt, overcome challenges, and generate unique solutions. It transcends the notion of simply creating art or music, extending to the creation of ideas, systems, and even ways of thinking that can significantly alter the course of history.
Creativity is not confined to a single form or method. It is not about merely producing something visually appealing or intellectually stimulating. It involves a deep connection to one’s inner thoughts and an openness to the unknown. The true essence of creativity lies in the process of discovery, the exploration of possibilities, and the courage to try the untried. Those who embrace creativity can carve new paths, often leading to remarkable breakthroughs and innovations that benefit society as a whole.
The current landscape of creativity is profoundly influenced by digital technology. The advent of artificial intelligence, for instance, has opened new realms of creative expression, allowing individuals to experiment with tools that were once out of reach. However, despite these advancements, the core principle of creativity remains unchanged—it is about finding new ways to express the inexpressible, to communicate complex ideas in simple terms, and to explore the boundless potential within each person.
The Power of Storytelling in Shaping Perception
In every culture, across all epochs, storytelling has played an integral role in shaping human understanding and conveying complex truths. From the earliest cave paintings to modern cinema, stories have always been a medium for transmitting wisdom, preserving history, and igniting emotions. They are more than just narratives; they are the foundation upon which societies build their values, beliefs, and collective identities.
Storytelling is one of the oldest human traditions, a powerful tool for education and entertainment. Yet, its true power lies in its ability to shape perception. How we tell stories, and the stories we choose to tell, influence how we see the world and ourselves. The stories that dominate our media, culture, and conversations help define societal norms and expectations. They influence our actions, our ambitions, and our relationships.
The art of storytelling has evolved significantly with the advent of new media. Traditional forms of oral storytelling, which relied on face-to-face communication and human connection, have given way to digital platforms that allow stories to reach global audiences instantly. Nevertheless, the fundamental principles of storytelling remain constant: a compelling narrative, relatable characters, and an emotional connection with the audience. The ability to craft a story that resonates with people on a personal level is a rare and valuable skill. It is this skill that has allowed authors, filmmakers, and marketers to create movements, inspire change, and bring about revolutions.
The Role of Innovation in Advancing Human Progress
Innovation is the cornerstone of human advancement. It is through innovative thinking that we have been able to move from the discovery of fire to the exploration of space. Innovation is the engine driving progress in every industry, from healthcare to transportation, from education to agriculture. It is not merely about inventing new gadgets or technologies; it is about challenging the status quo, asking questions, and seeking better ways to solve problems.
At its core, innovation requires an open mind and a willingness to take risks. The path to groundbreaking discoveries is rarely linear. It is often paved with failures, detours, and setbacks. However, each failure provides valuable lessons that bring innovators closer to their goals. The willingness to fail and learn from mistakes is what separates true innovators from those who merely follow established paths.
One of the most fascinating aspects of innovation is its ability to transform society. A single invention or idea has the potential to disrupt entire industries, change economies, and improve the quality of life for millions. The most influential innovations in history, such as the printing press, the steam engine, and the internet, have had far-reaching consequences that continue to shape the world in profound ways. In the modern world, we are witnessing the rise of technologies such as artificial intelligence, biotechnology, and renewable energy, all of which promise to revolutionize various aspects of human existence.
Innovation is also essential for addressing the global challenges we face today. Climate change, poverty, and inequality are problems that require innovative solutions. The next generation of innovators will need to think creatively and collaboratively to develop strategies that ensure a sustainable and equitable future for all.
The Significance of Emotional Intelligence in Personal Growth
Emotional intelligence (EI) is a key determinant of success in both personal and professional realms. Unlike traditional forms of intelligence, which focus on cognitive abilities, emotional intelligence revolves around understanding and managing one’s emotions and the emotions of others. It encompasses a range of skills, including self-awareness, empathy, self-regulation, and social awareness. These skills enable individuals to build meaningful relationships, navigate social complexities, and make decisions that align with their values and goals.
The significance of emotional intelligence lies in its ability to enhance communication and conflict resolution. In a world that is becoming increasingly interconnected, the ability to relate to others, understand their perspectives, and respond empathetically is more valuable than ever. High emotional intelligence allows individuals to create environments of trust, cooperation, and mutual respect, whether in a personal relationship, a team at work, or a global community.
Self-awareness, the foundation of emotional intelligence, is the ability to recognize one’s own emotions and how they affect thoughts and behaviors. This self-awareness enables individuals to make more informed decisions, control impulses, and react appropriately to different situations. By understanding their emotions, people can better navigate challenging circumstances and maintain a sense of balance.
Empathy, another critical component of emotional intelligence, allows individuals to connect with others on a deeper level. It involves recognizing and understanding the emotions of others, which in turn fosters stronger interpersonal bonds and enhances collaboration. Empathy is also crucial for effective leadership, as it helps leaders to motivate, inspire, and support their teams in meaningful ways.
The Role of Education in Shaping Future Generations
Education is one of the most powerful tools for shaping the future of society. It provides individuals with the knowledge, skills, and values necessary to navigate the world and contribute meaningfully to their communities. However, education is not just about academic achievement; it is about preparing individuals to think critically, solve problems, and adapt to an ever-changing world.
In today’s fast-paced, technology-driven society, education must go beyond traditional classroom learning. It must foster creativity, collaboration, and adaptability. The future will demand individuals who are not only knowledgeable but also capable of thinking critically, working in diverse teams, and innovating in the face of uncertainty.
Education also plays a pivotal role in addressing societal issues such as inequality and injustice. By providing equal access to quality education, societies can empower individuals from all backgrounds to achieve their full potential. Education is the great equalizer, offering opportunities for social mobility and the chance to break free from the constraints of poverty and disadvantage.
In the 21st century, education must adapt to the needs of a globalized world. Technology is reshaping how we learn, making information more accessible and interactive than ever before. Online platforms, digital tools, and virtual classrooms are transforming traditional educational models, allowing for greater flexibility and inclusivity. As these changes continue to unfold, education systems must ensure that they remain relevant and responsive to the needs of future generations.
The Intersection of Technology and Human Connection
In the modern world, technology has become inextricably linked to human interaction. From social media platforms to virtual meetings, technology has transformed the way we communicate, collaborate, and build relationships. While these advancements have undoubtedly made it easier to connect with others, they have also raised important questions about the nature of human connection in the digital age.
On the one hand, technology has bridged distances, enabling people to interact with others from different cultures, backgrounds, and locations. It has made it possible for individuals to share their ideas, experiences, and perspectives with a global audience. In many ways, technology has created new avenues for fostering understanding and empathy between people who may otherwise never have met.
On the other hand, the proliferation of digital communication has also led to concerns about the quality of human connection. With the rise of social media, many people feel more isolated, despite being constantly connected to others online. The superficial nature of online interactions, coupled with the pressure to present a curated version of oneself, has contributed to feelings of loneliness and disconnection. In addition, the overuse of technology can lead to a loss of face-to-face interactions, which are essential for building deep, meaningful relationships.
As we continue to navigate the complexities of a digitally connected world, it is essential to strike a balance between leveraging the benefits of technology and maintaining genuine human connections. While technology can facilitate communication, it is ultimately up to individuals to ensure that their interactions are authentic and emotionally fulfilling.
Understanding the Assessment Process for CMMC Level 2 Certification
When an organization embarks on the journey toward obtaining CMMC (Cybersecurity Maturity Model Certification) Level 2 certification, the path can seem intricate and challenging. However, each stage in this process is designed to ensure that the organization has the necessary measures in place to secure Controlled Unclassified Information (CUI) and meets the stringent requirements of the Department of Defense (DoD). The core of this journey lies in the process of assessing conformity to security requirements, a pivotal phase in the certification process that examines whether an organization’s cybersecurity practices are both adequate and sustainable.
The assessment process for CMMC Level 2 focuses heavily on validating the alignment of security controls and practices with the NIST (National Institute of Standards and Technology) SP 800-171A framework. This framework outlines the specific guidelines that an organization must follow to secure CUI and protect it from unauthorized access, alteration, or destruction. This stage is not simply about compliance with a set of rules but is about ensuring the organization’s cybersecurity strategies are ingrained in its operational processes and continuously maintained over time.
The Role of the Lead Certified CMMC Assessor
At the center of the CMMC Level 2 assessment is the Lead Certified CMMC Assessor (CCA), a qualified professional tasked with overseeing the evaluation. The Lead CCA leads a team of assessors who are responsible for ensuring that the organization seeking certification (OSC) adheres to the required security measures. The Lead CCA is a pivotal figure, guiding the entire assessment to ensure that it follows the necessary standards and best practices.
The Lead CCA's job is to direct the process to ensure that each security control is examined thoroughly, considering all relevant aspects of the organization's operations. This role requires not only technical expertise but also a deep understanding of security protocols and how they should be applied in a real-world environment. The CCA must ensure the assessment process is consistent, objective, and based on evidence rather than assumptions or conjecture.
Ensuring Objectivity and Consistency in the Assessment
A key feature of the CMMC Level 2 assessment process is the emphasis on objectivity. The assessment is designed to be impartial and fact-based, ensuring that no external influence or bias affects the outcome. This impartiality is critical, as it ensures that the organization’s compliance with security requirements is evaluated purely based on evidence and without any external pressures.
Throughout the assessment, the team will gather objective evidence from various sources. These can include system configurations, security logs, audit trails, and interviews with key personnel within the organization. By focusing on collecting tangible proof, the assessment avoids any subjective interpretations of compliance and instead ensures that all findings are based on verifiable facts.
Additionally, the assessment follows the guidelines outlined in ISO/IEC 17020:2012, which outlines the criteria for conformity assessment bodies. These guidelines ensure that the assessment is not only impartial but also consistently applied across all organizations seeking certification. This helps maintain a uniform standard of evaluation, regardless of the organization’s size, industry, or complexity.
Evaluating the Depth and Scope of Security Controls
One of the more complex elements of the CMMC Level 2 assessment is the evaluation of the depth and coverage of the security controls implemented by the organization. The purpose of this step is not just to verify that controls are in place but to determine how thoroughly and consistently they are applied across the organization.
Security controls should be integrated into the organization’s overall business processes and embedded in its operational activities. This means that the CMMC assessors do not simply look for whether a control is technically configured or implemented; they also check whether it has been applied in practice and whether it functions as intended in the day-to-day operations of the organization.
The assessment team carefully examines each control’s implementation, taking into consideration how it interacts with other systems, policies, and procedures. It is essential for the team to understand the full context in which each control operates and to assess whether it provides the desired level of protection against potential risks and vulnerabilities. This often involves a combination of document reviews, system inspections, and interviews with personnel to ensure that all aspects of the control are properly understood and functioning.
Addressing External Service Providers and Third-Party Risks
As organizations increasingly rely on external service providers (ESPs) for cloud services, infrastructure management, and other IT functions, the CMMC Level 2 assessment must also account for the security practices of these third parties. ESPs, including those who hold FedRAMP (Federal Risk and Authorization Management Program) certifications or other relevant certifications, must comply with the same security standards required for CMMC Level 2 certification.
Incorporating ESPs into the security assessment adds a layer of complexity to the process. If the OSC relies on third-party service providers to handle sensitive data or manage critical systems, the assessment team must ensure that these providers also meet the necessary security requirements. This often means reviewing the security protocols and certifications of these external entities and ensuring that their practices align with the OSC’s cybersecurity strategy.
Failure to account for the security practices of ESPs can result in gaps in the overall security posture of the organization, leading to vulnerabilities that could undermine the integrity of CUI protection. This aspect of the assessment process ensures that the organization’s entire supply chain, including external vendors and service providers, adheres to the same rigorous security standards.
Aligning Documentation with Practices and Scope
A significant challenge during the CMMC Level 2 assessment process is ensuring that the documentation submitted by the OSC accurately reflects the security practices and scope of the organization’s operations. The documentation provided by the OSC must not only outline the security controls that have been implemented but also provide clear evidence of how these controls are applied in practice.
In some cases, discrepancies between the stated scope and the actual implementation of security measures may arise. These mismatches can lead to confusion or delays in the assessment process. The OSC must provide accurate, up-to-date documentation that aligns with the actual security practices being followed. This ensures that the assessment team can effectively evaluate the organization’s compliance and identify any areas where further work may be required.
The assessment team will work closely with the OSC to resolve any inconsistencies and ensure that the scope of the assessment accurately reflects all systems, processes, and personnel that handle CUI. This collaborative approach helps maintain the integrity of the assessment and ensures that all relevant aspects of the organization’s security posture are fully evaluated.
Gathering and Documenting Evidence for Compliance
A crucial part of the CMMC Level 2 assessment is the gathering and documentation of evidence that substantiates the organization’s compliance with security requirements. This evidence can take many forms, including written policies, security configurations, incident response plans, training records, and audit logs. The evidence collected during the assessment provides the foundation for the final report, which outlines the organization’s compliance status.
Throughout the process, the assessment team will interview key personnel, review security configurations, and analyze historical security data. This approach helps create a comprehensive picture of the organization’s cybersecurity practices and ensures that the evidence gathered is thorough and representative of the organization’s actual security posture. Each piece of evidence is carefully analyzed to verify that the security controls are functioning as expected and providing the necessary protection against potential risks.
In addition to providing proof of compliance, the evidence also helps identify any areas where improvements may be needed. If gaps or vulnerabilities are discovered, the assessment team will document these findings and provide recommendations for corrective actions. These findings become part of the final report and are essential for the organization to address before it can move forward with the certification process.
Completing the Assessment and Preparing the Final Report
Once all evidence has been gathered and analyzed, the assessment team, under the leadership of the Lead CCA, prepares a detailed final report. This report is a comprehensive document that outlines the findings of the assessment, including any areas of non-compliance, vulnerabilities, or potential risks.
The final report serves as an objective, fact-based account of the organization’s cybersecurity practices and provides a roadmap for addressing any identified issues. If the organization is found to be in full compliance with CMMC Level 2 requirements, the report will reflect this, confirming that the OSC is ready for certification. If there are areas where the organization falls short, the report will detail the necessary corrective actions and provide guidance on how to resolve the issues.
The completion of the assessment and the finalization of the report mark a significant milestone in the CMMC certification journey. However, the process does not end there. Organizations must take the report’s findings seriously, addressing any gaps or vulnerabilities to ensure that they are fully compliant and capable of protecting sensitive information.
The Cybersecurity Maturity Model Certification (CMMC) is a rigorous framework that has been designed to enhance the security and integrity of the defense supply chain. It sets a series of standards to protect Controlled Unclassified Information (CUI) and ensure that organizations follow industry best practices. CMMC comprises multiple levels of security maturity, with Level 2 being a crucial milestone for many organizations in the Department of Defense (DoD) ecosystem. As businesses work towards obtaining CMMC certification, a significant step in the process involves the completion of a detailed assessment. This assessment ensures that an organization has met the necessary security requirements and is prepared to handle sensitive information securely. Following this assessment, the focus shifts to finalizing the evaluation and compiling the results in a structured manner.
The Role of the Lead CCA in the Assessment Process
The Lead Certified CMMC Assessor (Lead CCA) plays an essential role in overseeing the entire certification journey. Their responsibility is not just limited to conducting the assessment but extends to the critical task of synthesizing the findings and preparing the final report. The Lead CCA ensures that the assessment is thorough, unbiased, and in alignment with CMMC guidelines. This individual is the point of contact for any questions related to the assessment and is the key figure in compiling the data from the team of assessors.
Once the assessment phase concludes, the Lead CCA must ensure that the findings are documented coherently. This includes evaluating whether the Organization Seeking Certification (OSC) has met the security requirements stipulated by CMMC Level 2. The Lead CCA works to ensure that all relevant data points, such as vulnerabilities or non-compliance issues, are clearly identified and included in the final report. The report should be informative and accessible, offering a clear picture of the OSC’s cybersecurity posture.
Preparing the Final Report for the CMMC Assessment
The assessment report is one of the most critical documents in the certification process. It provides a comprehensive analysis of the OSC's cybersecurity infrastructure and identifies any gaps that may exist in their security protocols. The report does not simply offer a binary "pass or fail" evaluation but provides an in-depth breakdown of the findings, outlining specific areas where the OSC meets or falls short of the CMMC Level 2 requirements.
In preparing the report, the Lead CCA must ensure that the content is not only accurate but also understandable for a wide audience. While the Department of Defense and other stakeholders may have a high level of technical knowledge, the OSC itself may not always be equipped to interpret highly technical jargon. Therefore, the report should strike a balance between technical precision and clarity, enabling all parties to understand the significance of the findings and recommendations. The final report also serves as a reference document that can be used in future assessments and audits.
Identifying Gaps and Areas for Improvement
One of the key purposes of the CMMC assessment is to uncover any weaknesses or gaps in the OSC’s cybersecurity practices. These gaps can be diverse and may range from technical issues, such as outdated software, to organizational weaknesses like insufficient personnel training. The role of the assessment team is to conduct a meticulous review of the OSC’s practices, looking at everything from physical security measures to compliance with the necessary cybersecurity controls.
When weaknesses are identified, they must be clearly documented in the final report. This includes providing context for why the issue is important and how it might affect the organization’s overall security posture. Non-compliance issues should be outlined with sufficient detail, allowing the OSC to understand what corrective actions need to be taken. The report should also include the severity of each issue, enabling the OSC to prioritize remediation efforts effectively.
Developing a Plan of Action and Milestones (POA&M)
Once the assessment report is complete, the next step involves creating a Plan of Action and Milestones (POA&M). This document is vital for addressing any issues identified in the assessment and establishing a clear path forward. The POA&M outlines the specific corrective actions that need to be taken, along with timelines for each action. By developing this plan, the OSC can demonstrate a proactive approach to addressing security vulnerabilities and moving towards full compliance with CMMC Level 2.
The POA&M should be highly detailed, listing out the steps needed to remedy each identified weakness. Additionally, the document should include milestones for each action item, making it easier to track progress over time. This approach ensures that the organization is not only addressing immediate concerns but is also building a long-term strategy for continuous improvement. Once the POA&M is developed, it becomes an integral part of the overall certification process, ensuring that any gaps identified in the assessment phase are closed systematically.
Official Exit Meeting and Next Steps
After the assessment findings are documented and the POA&M is created, the next phase in the CMMC Level 2 certification process is the exit meeting. This meeting is held between the assessment team, the Affirming Official of the OSC, and other relevant stakeholders. It serves as an opportunity for the assessment team to walk through the findings and discuss the immediate next steps.
During the exit meeting, the assessment team will provide the OSC with a detailed review of their cybersecurity posture and any recommended actions. This meeting is essential for ensuring that the OSC fully understands the findings and is equipped to take the necessary steps toward remediation. If there are areas where the OSC has failed to meet CMMC Level 2 requirements, the team will outline the necessary corrective actions and guide how to proceed.
Additionally, the exit meeting provides an opportunity to discuss timelines for implementing corrective actions and schedule any follow-up assessments, if needed. The Lead CCA will ensure that the documentation is unambiguous, so that the OSC knows exactly what they need to do to move forward in the certification process.
Issuance of the CMMC Certification
If the OSC has successfully addressed the identified issues and met all the required standards, the assessment team will recommend certification. At this stage, the third-party assessment organization (C3PAO) will initiate the process of issuing the official Certificate of CMMC Status. This marks the culmination of the assessment phase and the OSC’s achievement of the CMMC Level 2 certification.
The issuance of the certificate is an important milestone for the OSC, as it demonstrates its commitment to maintaining high standards of cybersecurity. However, it is important to note that certification is not the end of the process. Post-assessment activities are essential to ensuring that the organization continues to meet the necessary standards and maintains compliance over time. This includes regularly reviewing and updating the POA&M, as well as conducting periodic internal assessments to ensure that new vulnerabilities or risks are identified and mitigated.
In conclusion, the process of finalizing the CMMC Level 2 certification involves a careful and thorough evaluation of the OSC’s cybersecurity practices. By documenting the assessment findings, identifying weaknesses, and creating a detailed plan for remediation, organizations can move forward with confidence. The support of the Lead CCA and the C3PAO ensures that the certification process is structured, transparent, and ultimately beneficial to the OSC's cybersecurity framework.
The path to achieving Cybersecurity Maturity Model Certification (CMMC) Level 2 represents a significant milestone for organizations striving to meet stringent security requirements, particularly those engaging with the Department of Defense (DoD). In the modern landscape, where cyber threats are continuously evolving, securing sensitive data has never been more critical. The CMMC framework offers a comprehensive approach to improving an organization’s cybersecurity practices, safeguarding the nation’s defense infrastructure, and fostering trust between contractors and the DoD.
The journey toward attaining CMMC Level 2 certification is both detailed and rigorous, designed to ensure that contractors meet specific cybersecurity requirements that protect Controlled Unclassified Information (CUI). While it requires substantial commitment from the Organization Seeking Certification (OSC), the benefits are profound, opening avenues for securing DoD contracts and ensuring long-term cybersecurity resilience. The final stages of this process, from completing the assessment to issuing the official certificate, involve various key actions that confirm the OSC’s compliance with all necessary cybersecurity protocols.
The Role of the C3PAO and the Authorized Certifying Official
The CMMC certification process is managed and executed by the Certified Third-Party Assessment Organizations (C3PAOs), which are responsible for evaluating the OSC’s cybersecurity posture against the established CMMC standards. These organizations are authorized to conduct assessments, make determinations, and issue certifications, ensuring that the process maintains objectivity and credibility.
At the heart of the finalization process is the Authorized Certifying Official (ACO), an essential role in ensuring that the CMMC certification process is completed correctly and that all criteria are met. The ACO is tasked with reviewing all relevant documentation that provides evidence of an OSC's compliance. This includes a thorough analysis of the results from the security assessment, the Plan of Action and Milestones (POA&M), and any corrective actions the OSC has undertaken to address weaknesses identified during the assessment phase.
The ACO’s duties go beyond administrative reviews. They must ensure that the OSC has fully addressed any remaining concerns, including verifying that all necessary remediation actions have been implemented according to the established timelines. This careful attention to detail is essential to maintaining the integrity and transparency of the certification process.
Final Assessment Review: Ensuring Compliance
Once the assessment team has completed its work, the final review is a pivotal moment in the certification process. This review ensures that the OSC has met all necessary compliance requirements as outlined in the CMMC Level 2 standards. It is here that the Authorized Certifying Official (ACO) plays a crucial role in confirming that all criteria are satisfied before the certification is granted.
The review includes a comprehensive check of the OSC’s cybersecurity practices and any changes made since the initial assessment. It is essential to verify that all open issues have been addressed, whether through the completion of remediation actions or by rectifying previously identified vulnerabilities. This process involves ensuring that all policies, controls, and procedures are in place and functioning as expected, so the OSC can demonstrate its ability to maintain a secure environment over time.
The final review is also critical for ensuring that the assessment was conducted fairly and impartially. This is where the C3PAO's Quality Assurance (QA) individual steps in. The QA individual reviews all steps in the assessment process, checking for adherence to established procedures, the thoroughness of the evaluation, and the integrity of the findings. This ensures that the certification process maintains a high standard of credibility, ensuring that only those organizations that genuinely meet the CMMC standards are granted certification.
Issuing the Certificate of CMMC Status
After completing all necessary checks, reviews, and verifications, the C3PAO can officially issue the Certificate of CMMC Status. This certificate signifies that the OSC has successfully met the CMMC Level 2 requirements, which encompass a broad range of cybersecurity practices aimed at protecting sensitive information. The certificate itself is more than just a piece of paper; it serves as a formal recognition of the OSC’s commitment to cybersecurity and its ability to safeguard the DoD’s data.
The issuance of the certificate is not merely a formality but an essential milestone for the OSC. It enables the organization to conduct business with the DoD and other government agencies that require CMMC certification for cybersecurity assurance. This document acts as an official credential, helping OSCs demonstrate their readiness to engage in defense-related work while assuring the DoD and other stakeholders of the organization's security posture.
It is important to note that CMMC certification is not a one-time achievement. While receiving the certification represents a significant accomplishment, maintaining that certification requires ongoing diligence. The OSC must continue to follow the necessary security protocols, complete regular assessments, and ensure compliance with the evolving CMMC standards. This ongoing commitment is crucial for maintaining business opportunities with the DoD and upholding the integrity of the certification.
The Importance of Maintaining Compliance After Certification
The process of obtaining CMMC Level 2 certification is demanding, but the responsibility does not end once the certificate is issued. In fact, maintaining compliance is just as critical as achieving certification in the first place. Organizations must be vigilant in continuously assessing their cybersecurity practices and implementing improvements as necessary. This ongoing effort ensures that they remain in line with the DoD's evolving security requirements and that they continue to protect sensitive information from emerging cyber threats.
To maintain their certification, OSCs are subject to periodic audits and assessments that ensure their cybersecurity measures are up to date and functioning correctly. These audits may be scheduled or may occur in response to a specific incident or change in regulations. Regular reviews of the organization's cybersecurity posture help identify any gaps that may have developed since the last assessment and allow for corrective measures to be taken promptly.
Moreover, as the cybersecurity landscape is continuously changing, the CMMC framework itself will likely undergo updates to address new threats, technologies, and best practices. OSCs must stay abreast of these updates and adapt their practices accordingly to ensure ongoing compliance with the latest standards. Failure to do so could result in a loss of certification, which would jeopardize the organization’s ability to engage with the DoD and other government entities.
Leveraging Certification for Business Opportunities
For an OSC, achieving CMMC Level 2 certification can be a gateway to numerous business opportunities, particularly within the defense sector. With CMMC certification becoming a mandatory requirement for contractors and subcontractors working with the DoD, having the certificate can significantly enhance an organization’s competitiveness and marketability.
The ability to prove compliance with the rigorous cybersecurity standards required by CMMC Level 2 helps build trust with potential clients, particularly those within the defense industry. Organizations that hold the certification are viewed as credible, secure, and capable of protecting sensitive government data, which makes them highly attractive partners for DoD contracts. This trust is a critical factor in winning contracts, as the DoD and other agencies place immense value on the security of their supply chains.
Additionally, the process of preparing for CMMC certification often helps organizations strengthen their internal cybersecurity frameworks. By aligning with industry-leading standards, organizations gain a better understanding of their own vulnerabilities and areas for improvement. This not only benefits the OSC in terms of securing DoD contracts but also enhances its overall security posture, which can be beneficial in other areas of business as well.
The Future of CMMC Certification and Cybersecurity Standards
As cybersecurity continues to be a priority in both public and private sectors, the CMMC framework will likely evolve to keep pace with the changing landscape of cyber threats. Organizations that achieve CMMC Level 2 certification will be better positioned to meet the challenges of the future, as the certification process helps to cultivate a culture of continuous improvement and proactive security measures.
In the coming years, it is anticipated that the DoD and other government agencies will continue to refine their cybersecurity requirements. This could mean updates to the CMMC standards, with increased focus on new technologies, emerging cyber threats, and enhanced risk management strategies. For OSCs, this presents both a challenge and an opportunity. Those who remain committed to maintaining compliance and improving their cybersecurity practices will continue to thrive in a rapidly changing environment.
As CMMC certification becomes more widespread and integrated into the defense industry’s supply chain, it will likely set a benchmark for other sectors as well. Organizations outside of the defense industry may adopt similar cybersecurity standards, recognizing the importance of securing sensitive information and protecting their operations from cyber threats. This growing emphasis on cybersecurity will only increase the value of CMMC certification, making it a powerful credential for organizations seeking to build credibility, trust, and resilience in the face of evolving risks.
Conclusion
Achieving and maintaining CMMC Level 2 certification is an ongoing journey that requires dedication, vigilance, and a proactive approach to cybersecurity. The process involves multiple phases, from the initial assessment to final certification, all of which are designed to ensure that the OSC meets the necessary standards for protecting sensitive information and maintaining the security of defense-related systems. Once certification is granted, it opens doors to business opportunities within the DoD and beyond, but it also places a continuous responsibility on the organization to uphold the highest cybersecurity standards. As cybersecurity threats continue to evolve, so too must the organizations that seek to protect themselves and their clients. Maintaining compliance with the CMMC framework is not just a requirement; it is a commitment to cybersecurity excellence that ensures long-term success and resilience in a dynamic and challenging digital world.
Frequently Asked Questions
How does your testing engine works?
Once download and installed on your PC, you can practise test questions, review your questions & answers using two different options 'practice exam' and 'virtual exam'. Virtual Exam - test yourself with exam questions with a time limit, as if you are taking exams in the Prometric or VUE testing centre. Practice exam - review exam questions one by one, see correct answers and explanations).
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Pass4sure products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Pass4sure software on?
You can download the Pass4sure products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email sales@pass4sure.com if you need to use more than 5 (five) computers.
What are the system requirements?
Minimum System Requirements:
- Windows XP or newer operating system
- Java Version 8 or newer
- 1+ GHz processor
- 1 GB Ram
- 50 MB available hard disk typically (products may vary)
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.