Certification: Certified CA Identity Manager Professional
Certification Full Name: Certified CA Identity Manager r12.x Professional
Certification Provider: CA Technologies
Exam Code: CAT-340
Exam Name: CA Identity Manager r12.x Professional
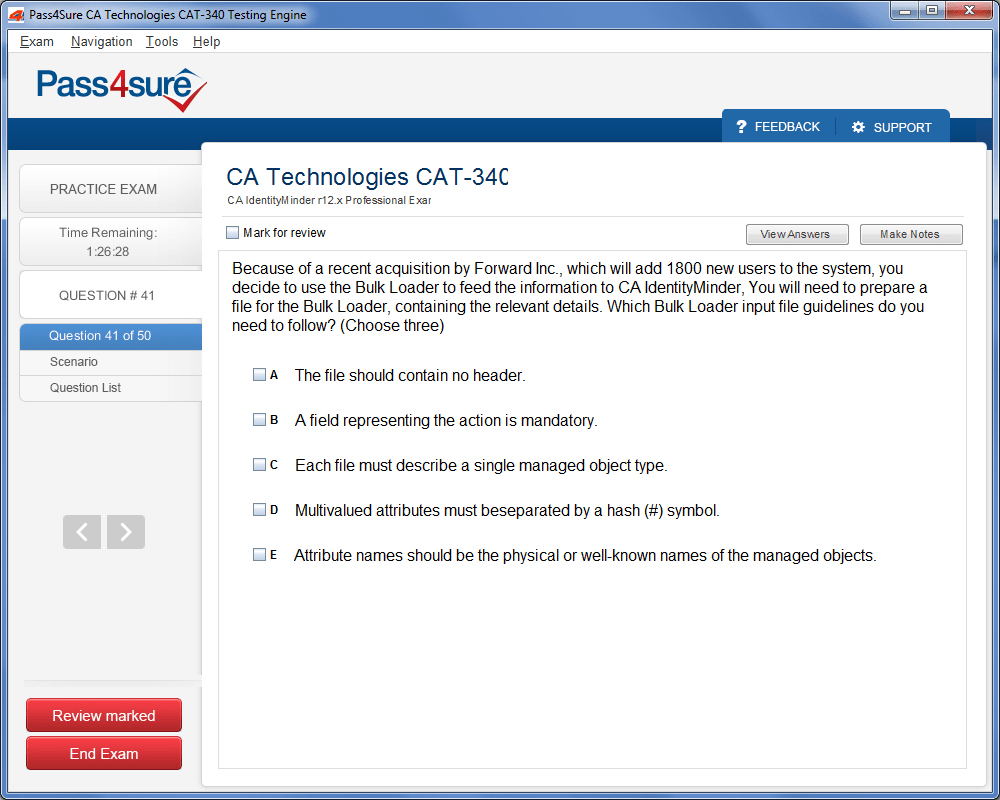
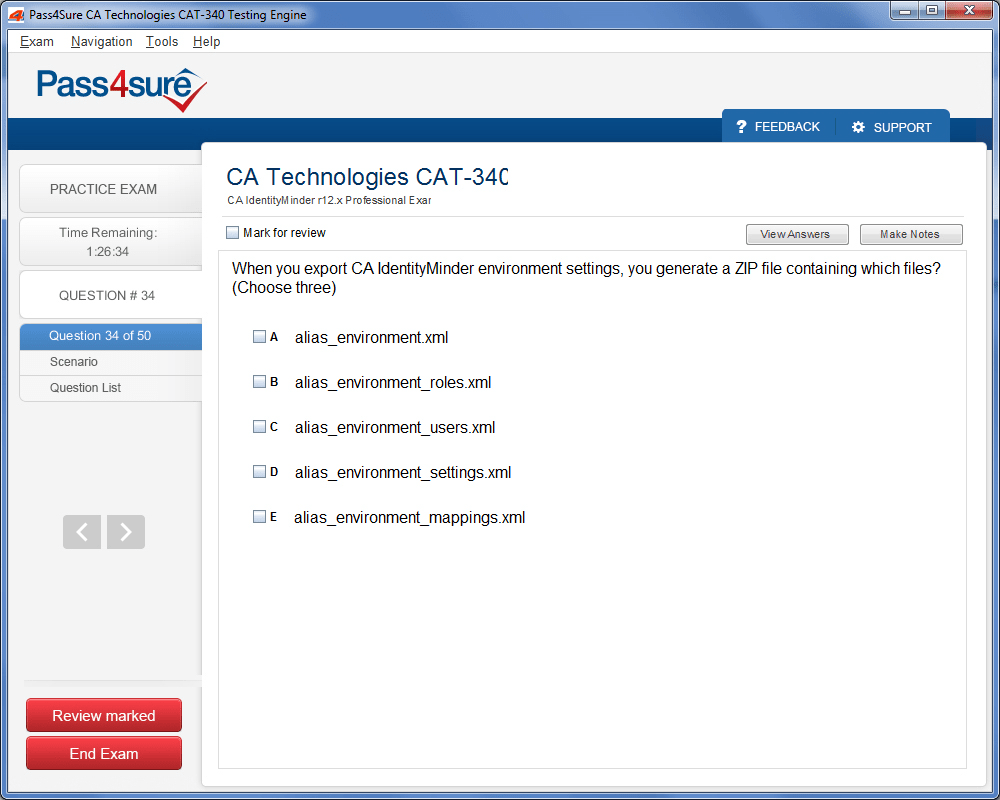
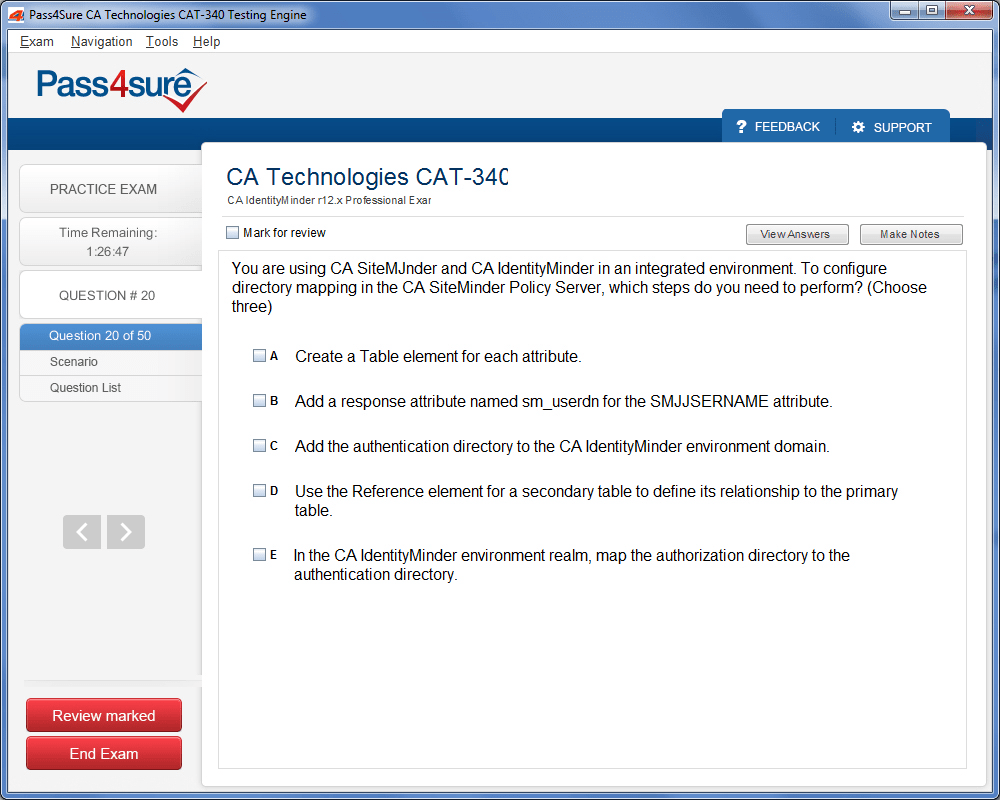
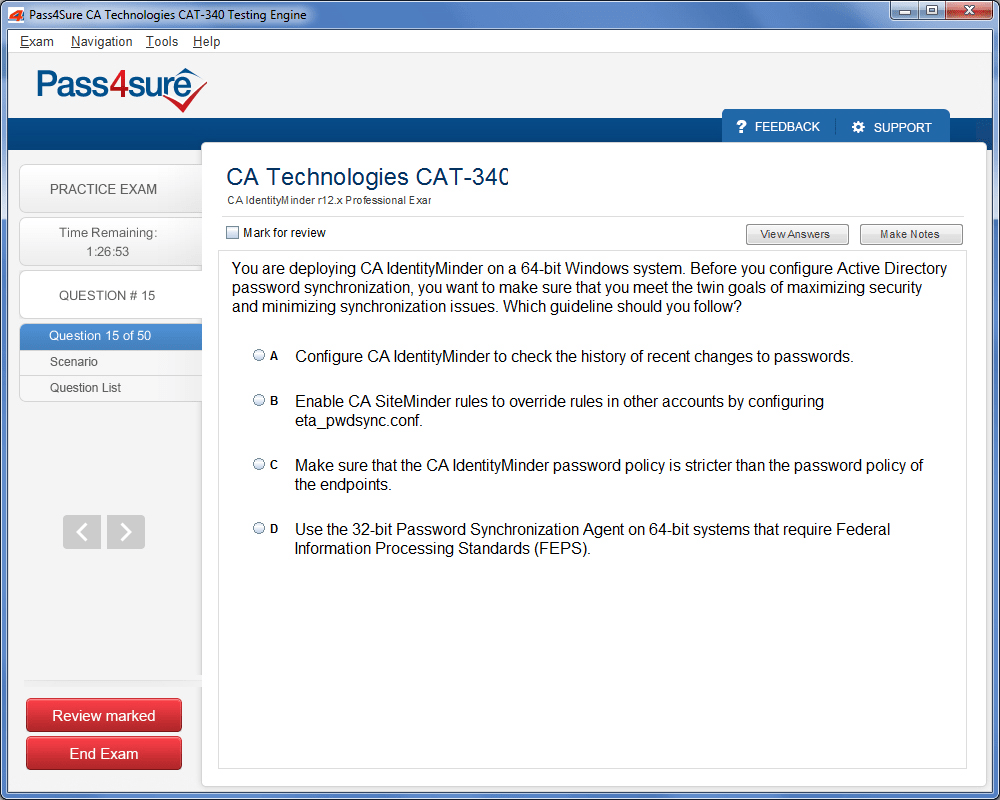
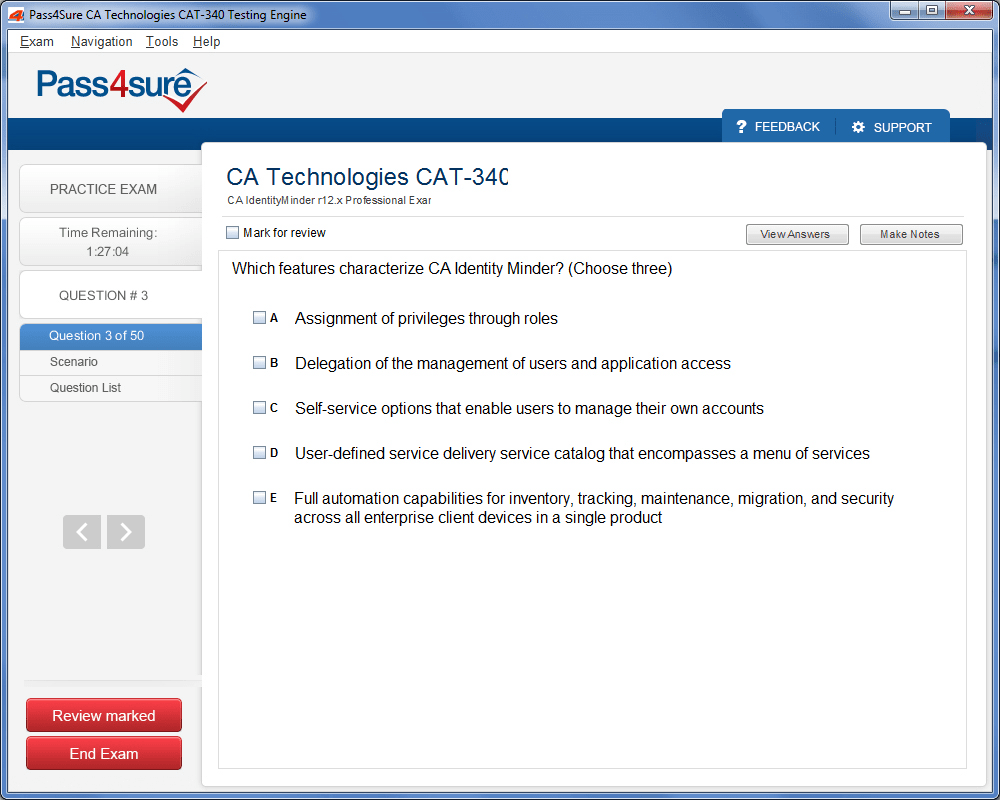
CAT-340 Exam Product Screenshots
Certified CA Identity Manager Professional: A Complete Guide to Modern Identity Management
In today’s interconnected digital world, organizations face unprecedented complexity in managing user identities, access permissions, and security protocols. The proliferation of cloud-based applications, remote workforces, and regulatory obligations has made traditional approaches insufficient. Enterprises no longer operate in isolated silos; they exist in a dynamic ecosystem where data flows freely across platforms and devices. This interconnectedness brings convenience and efficiency, but it also magnifies the risk of security breaches, compliance violations, and operational inefficiencies. Professionals trained in Certified CA Identity Manager Professional principles understand that identity management is not merely a technical function; it is the backbone of organizational security and operational resilience.
The challenges organizations encounter are multifaceted. Workforce mobility, temporary contractors, mergers, and acquisitions constantly alter the identity landscape. Every change requires meticulous attention to access rights, entitlements, and compliance mandates. Errors in identity governance can result in unauthorized access, data leaks, and reputational damage. To navigate this complexity, organizations need centralized systems that streamline identity lifecycle management. Certified CA Identity Manager Professional expertise empowers professionals to design, implement, and manage these systems with precision, ensuring that identities are consistently monitored, governed, and protected across the enterprise.
Automation and Workflow Optimization in Identity Governance
Automation lies at the heart of modern identity management. Manual processes are labor-intensive and prone to errors, which can introduce vulnerabilities into even the most secure environments. Professionals certified in CA Identity Manager understand how to create automated workflows that handle user provisioning, de-provisioning, and access adjustments with minimal human intervention. By defining explicit roles, permissions, and approval hierarchies, organizations can ensure that new employees are granted the right level of access from day one, while departing employees have their access revoked immediately, minimizing exposure.
Beyond basic provisioning, automated workflows allow for complex scenarios such as temporary access, multi-tier approval processes, and dynamic entitlement adjustments. This precision reduces operational bottlenecks and enhances compliance with internal policies and external regulations. Automation also ensures auditable trails for every access event, making it easier for organizations to demonstrate adherence to standards during audits or regulatory inspections. Certified CA Identity Manager Professional training emphasizes these practices, equipping professionals to design systems that balance operational efficiency with rigorous security requirements.
Identity Lifecycle Management and Access Review
Identity lifecycle management is a continuous process, extending well beyond initial provisioning. It involves ongoing monitoring, role maintenance, access reviews, and policy enforcement. Professionals in this field recognize that access rights are not static; they evolve with organizational changes, departmental restructuring, and project-specific requirements. Certified CA Identity Manager Professional methodologies emphasize regular reconciliation of entitlements to ensure that permissions align with current roles and responsibilities.
Access reviews are a critical component of this process. Periodic assessment of user access allows organizations to identify and remove redundant or inappropriate permissions before they become security risks. Skilled professionals leverage analytics and reporting tools to detect anomalies, unusual access patterns, or potential insider threats. By incorporating predictive insights, they can anticipate risky behaviors and intervene proactively. This approach transforms identity governance from a reactive measure into a proactive discipline, safeguarding critical assets while fostering operational agility.
Integration Across Diverse IT Environments
Modern organizations operate across heterogeneous IT environments, blending on-premise infrastructure with cloud services and hybrid platforms. Effective identity management requires seamless integration across these diverse systems. Certified CA Identity Manager Professional experts possess the technical acumen to ensure that provisioning, authentication, and access control mechanisms operate consistently, regardless of platform or environment. This integration reduces friction for end-users while maintaining a robust security posture, enhancing both productivity and compliance.
Integration extends beyond technical connectivity. It includes unifying reporting, auditing, and monitoring systems to provide comprehensive visibility into identity and access activities. Organizations gain clarity on who has access to what, when changes occurred, and how policies are enforced. Such transparency is essential for internal stakeholders, auditors, and regulators. Professionals skilled in CA Identity Manager principles design integration strategies that harmonize multiple systems, ensuring operational continuity without compromising security or efficiency.
Policy Enforcement and Organizational Alignment
Policy enforcement is an intricate element of identity governance. While technology can automate many tasks, effective policy implementation requires alignment with organizational culture, operational workflows, and regulatory expectations. Certified CA Identity Manager Professional training emphasizes the importance of creating policies that are enforceable, adaptable, and aligned with strategic objectives. By incorporating rule-based automation, the system can handle routine operations autonomously while escalating exceptional cases for human review, striking a balance between efficiency and oversight.
Policies cover a broad spectrum of governance functions, including password management, access approvals, and compliance reporting. Professionals must anticipate scenarios where exceptions are necessary and design mechanisms to address them without compromising overall security. The result is a dynamic policy framework that evolves alongside organizational needs, enabling identity governance to remain resilient in the face of change. This capability ensures that enterprises maintain compliance, minimize risk, and support operational flexibility simultaneously.
The Human Element in Identity Management
Despite the sophistication of automated systems, human behavior remains a pivotal factor in identity governance. Training, awareness, and communication are essential complements to technological solutions. Professionals certified in CA Identity Manager recognize that employees, contractors, and partners must understand their responsibilities in protecting digital assets. Misunderstanding, negligence, or inadvertent errors can undermine even the most advanced identity management systems. Engaging users through education programs enhances compliance, reduces risky behaviors, and fosters a culture of security mindfulness.
Human-centered strategies also include clear communication of policy changes, real-time alerts for anomalous activities, and intuitive access workflows. By combining technical controls with user engagement, organizations cultivate an environment where identity management practices are understood, respected, and consistently followed. Professionals in this space bridge the gap between technology and human behavior, ensuring that identity governance is effective in real-world operational contexts.
Leveraging Emerging Technologies in Identity Governance
Emerging technologies, including artificial intelligence, machine learning, and predictive analytics, are reshaping the landscape of identity management. Certified CA Identity Manager Professional expertise enables organizations to integrate these innovations effectively, enhancing proactive security measures. Machine learning models can detect subtle deviations in user behavior, identify potential access violations before they occur, and suggest optimized workflows to minimize risk. Predictive analytics help organizations anticipate challenges in identity governance, allowing them to allocate resources efficiently and preemptively address vulnerabilities.
These technologies also facilitate real-time monitoring and anomaly detection at scale, which is increasingly important as organizations expand their digital footprint. Professionals trained in CA Identity Manager principles are adept at leveraging these tools without compromising operational simplicity or user experience. By combining automation, human oversight, and intelligent analytics, enterprises achieve a more resilient, adaptive, and forward-looking identity management ecosystem. This integration ensures not only regulatory compliance but also strategic advantage, as organizations can confidently operate in complex, dynamic digital environments.
Understanding the Landscape of Modern Identity Governance
In contemporary enterprises, the concept of identity governance stretches far beyond mere password management or login credentials. It encompasses the entire lifecycle of digital identities, from onboarding to offboarding, and the orchestration of access privileges across multifaceted systems. Modern organizations operate in intricate digital ecosystems where employees, contractors, and partners interact with numerous applications, databases, and platforms. Managing these interactions without a cohesive identity governance strategy introduces vulnerabilities that can undermine security, efficiency, and compliance.
At the heart of effective governance lies a keen understanding of enterprise processes. Each department, from finance to human resources, carries distinct access needs and sensitivities. A sophisticated identity governance approach requires mapping these needs accurately, assessing which users require access to specific resources, and understanding the risk associated with each entitlement. This level of precision ensures that operational workflows are not disrupted while maintaining a tight security posture.
Furthermore, identity governance is no longer a static function. As businesses evolve, roles transform, teams reconfigure, and projects conclude or commence. Without a dynamic framework, access privileges quickly become outdated, resulting in orphaned accounts, redundant permissions, or excessive exposure to sensitive data. Enterprise leaders increasingly recognize that governance must evolve as organically as the organization itself, responding to structural shifts, technological integration, and regulatory changes with agility and foresight.
Role-Based Access Control as a Cornerstone
Role-based access control (RBAC) has emerged as the cornerstone of modern identity governance. Instead of assigning permissions individually, enterprises classify users into roles that reflect their responsibilities, operational requirements, and compliance obligations. Each role serves as a blueprint, defining which resources are accessible, under what conditions, and for what purpose.
Creating roles with precision demands an intimate understanding of business processes. For instance, an employee in the finance department may require access to budgeting tools, expense tracking systems, and financial reporting applications. By contrast, a marketing professional may need permission to campaign management platforms, analytics dashboards, and content repositories. Role definition is not a one-time activity but a continuous refinement process. Organizations must adjust roles as employees shift responsibilities, projects evolve, or regulatory mandates change.
Dynamic role assignment further enhances efficiency. By automating the alignment of access privileges with an individual’s current role, enterprises reduce administrative overhead and minimize the risk of human error. Additionally, role hierarchies can enforce layered security, granting broad privileges only to senior staff while maintaining restricted access for junior personnel. In practice, a well-implemented RBAC system ensures that each user has precisely what they need—no more, no less—balancing operational productivity with stringent security.
Automating Access Reviews and Certification
Access reviews, or certification campaigns, are critical for maintaining a secure environment. They verify that users retain only the access necessary for their current responsibilities, eliminating outdated or unnecessary permissions that could serve as attack vectors. Traditionally, these reviews were labor-intensive, relying on manual spreadsheets and email notifications that consumed valuable time and introduced errors.
Automation transforms this process into a streamlined, reliable function. Modern identity governance solutions enable periodic, rule-driven review cycles, presenting managers with actionable insights and summary dashboards that highlight anomalies or potential risks. Automated reporting ensures that compliance teams have ready access to detailed records, satisfying audit requirements effortlessly. By embedding automation into access reviews, enterprises not only save resources but significantly reduce exposure to unauthorized access.
Moreover, automation supports continuous monitoring rather than periodic reviews alone. Systems can flag unusual access patterns, detect simultaneous logins from multiple locations, or highlight attempts to escalate privileges improperly. Proactive identification of these anomalies allows teams to intervene before minor discrepancies escalate into full-blown security incidents, reinforcing the organization’s risk management posture.
Integrating Identity Across Complex Systems
Modern enterprises rarely operate within a single, unified platform. Instead, they utilize a combination of on-premise systems, cloud applications, third-party services, and mobile platforms. Effective identity governance requires seamless integration across these diverse systems, ensuring that provisioning, de-provisioning, and access changes occur without friction or delay.
Integration begins with mapping identity sources. Directories, databases, and application-specific accounts must communicate cohesively, with standardized protocols and clear workflows. This technical interoperability is complemented by operational understanding. Teams must analyze departmental processes, pinpoint where access is needed, and anticipate the impact of changes on business continuity. By marrying technical integration with process insight, enterprises create a governance ecosystem that operates fluidly, regardless of the complexity or diversity of underlying systems.
In hybrid environments, cloud adoption introduces additional challenges. Cloud platforms often offer varying identity and access management capabilities, necessitating robust synchronization and policy enforcement mechanisms. Without careful integration, employees might encounter inconsistent access, delays in onboarding, or gaps in security coverage. Advanced identity governance solutions address these challenges by creating centralized policy management, enabling organizations to enforce consistent rules while retaining flexibility for diverse operational contexts.
Leveraging Analytics for Predictive Security
Data is at the core of modern identity governance, but raw information alone is insufficient. Enterprises must translate access logs, login histories, and entitlement changes into actionable intelligence. Analytics empowers security teams to identify patterns, detect anomalies, and predict potential threats before they materialize.
For instance, repeated failed login attempts, unusual access frequency, or abrupt changes in privilege assignment may signal compromised accounts. By employing predictive analytics, organizations can intervene preemptively, reducing risk and protecting sensitive data. Dashboards that consolidate this information in real time enable decision-makers to act swiftly, while historical analysis informs future policy adjustments.
Beyond risk detection, analytics also supports operational optimization. Insights derived from access patterns reveal redundancies, highlight underutilized resources, and identify opportunities for process improvement. Analytics thus transforms identity governance from a purely defensive measure into a strategic tool, helping enterprises optimize workflows, allocate resources efficiently, and maintain a vigilant stance against emerging threats.
Human-Centric Change Management
Identity governance is not solely a technical challenge; it is fundamentally an exercise in managing people, processes, and culture. Changes in workflows, access policies, or system interfaces can provoke confusion or resistance if not handled thoughtfully. Human-centric change management ensures that governance initiatives are embraced rather than circumvented.
Effective change management integrates communication, training, and phased deployment. Employees must understand why certain access controls exist, how new systems affect their daily activities, and what steps they need to take to comply with new protocols. Training programs can be tailored to different roles, focusing on practical application rather than abstract policy. By combining technical deployment with supportive guidance, organizations cultivate a culture of security awareness and operational accountability.
Phased rollouts further ease the transition. Rather than implementing sweeping changes abruptly, enterprises can pilot governance initiatives in specific departments, gather feedback, and refine processes before wider deployment. This iterative approach minimizes disruption, enhances user adoption, and allows technical teams to identify and resolve unforeseen issues proactively. In practice, human-centric change management ensures that identity governance initiatives are sustainable, resilient, and aligned with the broader organizational culture.
Embedding Governance Into Daily Operations
Identity governance should not exist as an isolated function executed sporadically; it must be embedded into the rhythm of daily operations. By integrating policy enforcement, access monitoring, and compliance reporting directly into routine workflows, enterprises achieve continuous security while maintaining operational efficiency.
This embedding transforms governance from a reactive mechanism into a proactive asset. Users receive timely guidance on appropriate access, anomalies are flagged in real time, and compliance reports are generated automatically. By treating identity governance as an ongoing operational activity rather than a periodic audit, organizations enhance security, streamline administrative processes, and create a transparent, accountable environment.
A mature governance model views the system as a living entity. Roles evolve, access permissions adjust dynamically, and analytics continuously refine security protocols. This adaptive posture ensures that enterprises remain agile in the face of organizational growth, technological innovation, and emerging threats. Security, efficiency, and compliance are not competing objectives but interwoven outcomes of a holistic identity governance framework.
Understanding Identity Lifecycle Management in Modern Organizations
Identity lifecycle management is the cornerstone of secure, efficient, and resilient organizational infrastructure. At its essence, it involves controlling, monitoring, and evolving digital identities from their inception through retirement. In a world where data breaches and cyber threats are increasingly sophisticated, organizations cannot afford static or reactive identity practices. By embracing comprehensive lifecycle management, institutions gain the ability to govern access consistently, mitigate risk proactively, and enhance user experiences across multiple systems. Professionals versed in advanced techniques recognize that identity is more than a credential—it is a dynamic entity that requires ongoing oversight, refinement, and strategic alignment with organizational goals.
The lifecycle begins with provisioning, the process of granting access to systems, applications, and resources. Yet, provisioning alone is insufficient. Identity management must anticipate changes in roles, responsibilities, and organizational structures. Lifecycle management accounts for onboarding, transfers, promotions, terminations, and even temporary assignments. By embedding foresight into identity processes, organizations can reduce operational friction and maintain a high level of security without interrupting productivity. This anticipatory approach transforms the management of identities from a series of tasks into a continuous, strategic discipline.
Entitlement Reconciliation and Access Accuracy
One of the most intricate elements of identity lifecycle management is entitlement reconciliation. Large organizations often operate multiple systems, each with distinct roles, permissions, and hierarchies. Without careful reconciliation, discrepancies arise, resulting in either overprivileged accounts or unintended access gaps. Professionals trained in advanced techniques employ automated mechanisms to compare expected entitlements with actual access continuously. These mechanisms detect inconsistencies, flag anomalies, and initiate workflows to correct deviations.
Reconciliation ensures that privileges align precisely with responsibilities, mitigating both security risks and compliance concerns. It also prevents the phenomenon known as privilege creep, where users accumulate unnecessary permissions over time due to role changes or system updates. By maintaining strict alignment between entitlements and actual needs, organizations uphold accountability and reduce the likelihood of unauthorized access. Furthermore, advanced reconciliation frameworks often include predictive elements, identifying potential conflicts before they materialize and enabling proactive interventions.
Policy-Driven Automation and Organizational Efficiency
Automation in identity lifecycle management extends far beyond task execution—it is a strategic enabler of compliance, accuracy, and efficiency. Policy-driven automation allows organizations to codify access rules that reflect organizational structures, security mandates, and business priorities. When policies govern access decisions, human error is minimized, approvals are expedited, and operational consistency is assured.
Consider a scenario in which an employee transitions to a new department. Policy-driven automation automatically revokes access to former resources while granting permissions appropriate to the new role. Exceptions can be accounted for through finely tuned rules, ensuring that flexibility does not compromise security. Organizations benefit from reduced administrative workload, while professionals maintain the ability to monitor and adjust automation to align with evolving priorities. The interplay of rules, automation, and governance exemplifies the sophistication inherent in modern identity lifecycle management.
Self-Service Interfaces and Delegated Administration
User-centric features significantly enhance the efficiency of identity management systems. Self-service interfaces empower individuals to request access, reset passwords, or update personal information without relying on centralized support teams. These capabilities increase adoption, reduce operational bottlenecks, and enhance user satisfaction. Advanced identity management specialists design these interfaces to be intuitive and aligned with organizational governance, balancing autonomy with control.
Delegation mechanisms complement self-service features by allowing managers or designated approvers to perform routine access adjustments while maintaining oversight. This creates a hierarchical flow where responsibility is distributed without compromising security. For example, a manager can approve temporary access for a project team without involving IT administrators directly, yet all actions remain logged and auditable. The combination of self-service and delegation exemplifies the modern philosophy of empowering users while preserving strict control, an approach that is foundational to advanced identity lifecycle management.
Auditing, Analytics, and Proactive Governance
Transparency and insight are critical to maintaining secure and compliant identity ecosystems. Advanced lifecycle management emphasizes auditing and analytics not merely as regulatory obligations but as tools for proactive governance. Dashboards and reporting frameworks provide visibility into access patterns, policy adherence, and potential vulnerabilities. High-risk accounts, irregular access requests, and anomalous behavior can be identified and addressed before incidents occur.
Analytics extend beyond detection, enabling strategic decision-making. By examining trends in user behavior, organizations can anticipate needs, optimize provisioning processes, and align access policies with evolving business requirements. Data-driven insights enhance operational efficiency while strengthening security posture. Professionals integrate monitoring frameworks with automated alerts and actionable reporting, ensuring that organizations are not just reacting to events but are equipped to prevent them. The fusion of audit transparency and predictive analysis underscores the sophistication of contemporary identity lifecycle management.
Integration of Emerging Technologies
The landscape of identity management is evolving rapidly with the advent of artificial intelligence, machine learning, and behavioral analytics. These technologies enable organizations to analyze large volumes of identity-related data, detect unusual patterns, and predict future risks with unprecedented accuracy. AI-driven identity systems can identify subtle anomalies that might elude manual review, such as gradual privilege escalation or atypical login behavior.
Integration of these technologies transforms identity management from a maintenance-focused task into a proactive, intelligent function. Organizations can anticipate threats, automate complex decision-making, and continuously refine their policies based on real-world data. This fusion of innovation and governance represents the next stage of identity lifecycle evolution, requiring professionals to blend technical expertise with strategic foresight. It ensures that identity systems remain resilient, adaptive, and capable of responding to rapidly changing security landscapes.
Human-Centered Design and Cultural Alignment
Even the most advanced technological solutions cannot achieve optimal results without considering the human element. Training, awareness programs, and effective communication are critical for ensuring that users understand their responsibilities within the identity lifecycle. By designing systems that are user-friendly and aligned with organizational culture, professionals enhance compliance, reduce errors, and foster engagement.
Human-centered design also applies to workflow customization, exception handling, and policy transparency. Users are more likely to comply with processes that are clear, predictable, and responsive to their needs. Similarly, managers and administrators benefit from systems that integrate oversight without introducing unnecessary complexity. The alignment of technological rigor with human behavior is a hallmark of mature identity lifecycle management, ensuring that security measures are effective, sustainable, and widely embraced.
Understanding Identity Management Systems
Identity management systems serve as the backbone of modern organizational operations. At their core, these systems handle the creation, maintenance, and deactivation of user identities, ensuring secure access to resources while maintaining compliance. The intricacies of identity management extend far beyond mere user authentication. They involve policy enforcement, lifecycle management, and integration across diverse technological landscapes. Professionals who specialize in this field must not only understand technical mechanisms but also possess strategic foresight to anticipate potential complications before they manifest.
In the contemporary digital environment, organizations rely on a blend of on-premise solutions, cloud infrastructures, and hybrid environments. This mixture demands robust identity management systems capable of maintaining coherent identity states across platforms. Discrepancies in user information or access privileges can cascade into operational inefficiencies and security vulnerabilities. Experts trained in advanced identity management practices approach these challenges with meticulous attention to detail, recognizing that every misalignment, however minor, can compromise system integrity.
Moreover, identity management encompasses both the administrative and experiential aspects of user interactions. While security remains paramount, systems must also accommodate user expectations for seamless access. Balancing these priorities requires careful orchestration of workflows, policy frameworks, and technical configurations. In this way, identity management becomes not just a technical endeavor but a dynamic operational discipline.
Integration Complexities in Hybrid Environments
Modern enterprises seldom operate within a single technological ecosystem. Legacy applications, cloud-based platforms, and emerging tools coexist, creating a heterogeneous environment that complicates identity synchronization. Integration challenges often manifest as delayed provisioning, incomplete de-provisioning, or inconsistent policy application. These issues can hinder operational continuity and frustrate end-users who rely on timely access to resources.
Professionals trained in identity management methodologies leverage analytical techniques to dissect these hybrid environments. They identify discrepancies between systems, trace their origins, and implement corrective workflows designed to maintain a unified identity state. Rather than addressing symptoms in isolation, this approach targets root causes, ensuring long-term stability.
Furthermore, integration requires continual monitoring and adaptation. Systems evolve, new applications are introduced, and organizational needs shift. Maintaining harmony across this landscape demands ongoing vigilance. Experts employ automation, routine audits, and strategic configuration adjustments to prevent integration errors from accumulating. The result is a seamless experience where users interact with multiple platforms without friction or confusion.
Optimizing System Performance
As organizations grow, identity management systems face increasing pressure from higher volumes of requests, approvals, and auditing processes. Performance bottlenecks can emerge, leading to delays that affect productivity and satisfaction. Optimization is therefore essential to maintain operational efficiency and system reliability.
Effective performance enhancement involves analyzing workflow structures, identifying redundancies, and implementing automation where appropriate. Professionals streamline approval chains, consolidate repetitive tasks, and apply predictive analytics to forecast demand spikes. These measures ensure that the system can accommodate high volumes without degradation in response times.
Additionally, performance optimization has a direct impact on user experience. Fast, reliable access encourages adherence to organizational protocols, reduces manual intervention by administrators, and fosters trust in the system. Organizations that neglect performance considerations often face a paradox: strong security measures that become impediments to daily operations, causing frustration and potential circumvention of established policies.
Experts also consider scalability during optimization. Systems must not only perform well today but remain capable of supporting growth in user population, application diversity, and regulatory requirements. Continuous refinement ensures that identity management infrastructure evolves in tandem with organizational demands, preventing performance issues from becoming systemic problems.
Navigating Policy Frameworks
Policies are the lifeblood of identity management. They define who has access to what, under which circumstances, and for how long. Yet policy misconfigurations are a subtle yet pervasive challenge. Rules that are too restrictive can impede workflow efficiency, while overly permissive configurations introduce vulnerabilities and compliance risks.
Professionals meticulously review and adjust policy frameworks, often combining automated verification with human oversight. Exception handling mechanisms are integrated to manage unique scenarios without undermining system integrity. This dual approach ensures that the organization remains secure while allowing flexibility for real-world operational requirements.
Policy management is not a static exercise. As regulations evolve and business needs shift, organizations must adapt policies accordingly. Continuous monitoring, regular audits, and proactive refinements are critical to maintaining relevance and effectiveness. Skilled professionals cultivate a deep understanding of both technical enforcement and strategic implications, ensuring that policy frameworks support operational goals rather than hinder them.
Moreover, policy clarity enhances compliance and reduces error rates. Well-defined rules minimize ambiguity, guiding users and administrators toward correct actions. Clear policies also simplify troubleshooting and incident resolution, as deviations from expected behavior can be quickly identified and rectified.
Incident Response and Risk Mitigation
Identity management systems are only as secure as their response mechanisms during anomalous events. Unauthorized access attempts, failed authentication sequences, or policy violations require immediate attention to prevent data compromise and operational disruption.
Experts develop proactive incident response protocols that combine automated alerting, escalation procedures, and remediation strategies. These measures ensure that potential threats are identified and contained promptly. Detailed logging supports retrospective analysis, enabling organizations to learn from incidents and refine both system configurations and operational procedures.
Rapid and structured responses not only mitigate immediate risks but also reinforce organizational confidence in identity management practices. Employees and stakeholders recognize that anomalies are addressed systematically, reducing panic and encouraging compliance with established protocols. This culture of preparedness transforms security from a reactive obligation into a proactive capability.
Incident response planning also considers user experience. While security must remain rigorous, interventions should minimize disruption to legitimate operations. Professionals carefully balance control and accessibility, ensuring that necessary protective measures do not become impediments to productivity. This nuanced approach underpins resilient, trustworthy systems that withstand both technical failures and human error.
Enhancing User Experience
Even technically flawless systems can fail if they are difficult to navigate or counterintuitive. User experience is a critical dimension of identity management, influencing adoption rates, compliance, and operational efficiency.
Designing intuitive interfaces and streamlined workflows helps users interact with the system effectively. Minimizing unnecessary steps, providing self-service capabilities, and offering contextual guidance fosters confidence and reduces dependency on administrative support. By embedding usability into system design, organizations achieve higher engagement while maintaining control over access and security.
User experience optimization is not merely cosmetic; it has tangible operational benefits. Smoother interactions reduce error rates, accelerate request processing, and decrease administrative workloads. Professionals leverage feedback loops and behavioral analytics to identify friction points, iteratively refining interfaces and processes. This commitment to usability transforms identity management from a restrictive tool into an enabler of efficiency and collaboration.
Furthermore, user-centered design promotes compliance. When processes are straightforward, users are less likely to seek workarounds or bypass protocols. Clear communication, accessible guidance, and responsive systems cultivate trust, reinforcing the organization’s overall security posture without resorting to cumbersome enforcement measures.
Continuous Improvement and Adaptive Frameworks
Identity management is not a set-and-forget endeavor. Continuous improvement is essential to maintain relevance, resilience, and operational excellence. Professionals employ metrics, user feedback, and technological insights to iteratively refine workflows, enhance integrations, and implement automation improvements.
Adaptive frameworks enable systems to evolve alongside organizational needs. Updates to workflows, policy refinements, and new integration modules are carefully assessed and implemented to ensure alignment with business objectives. This iterative mindset transforms identity management from a static infrastructure into a dynamic, living system capable of responding to emerging challenges.
Moreover, continuous improvement fosters innovation. By regularly evaluating system performance, security posture, and user satisfaction, organizations uncover opportunities for enhancement that might otherwise remain hidden. Professionals leverage these insights to optimize resource allocation, anticipate future needs, and maintain a competitive edge.
Investing in adaptive frameworks also mitigates long-term risks. Systems that evolve in a controlled, deliberate manner are less susceptible to cascading failures caused by outdated processes or misaligned policies. This proactive approach ensures that identity management remains robust, secure, and aligned with organizational priorities, even in the face of rapid technological change.
The Transformative Role of Identity Governance in Modern Enterprises
In today’s interconnected business ecosystem, the management of digital identities has emerged as a cornerstone for operational integrity and organizational resilience. Enterprises of every scale encounter a proliferation of access points, applications, and systems, making identity governance an indispensable function. Professionals who master identity management cultivate frameworks that harmonize security, efficiency, and compliance. By implementing meticulously designed access policies, they safeguard sensitive information while facilitating seamless workflows. This balance between control and agility becomes particularly significant as enterprises navigate evolving regulatory landscapes and technological complexity.
Identity governance extends beyond mere password management or user authentication. It encompasses a strategic orchestration of privileges, roles, and approvals that ensures each digital identity aligns with organizational objectives. Professionals meticulously analyze access patterns, anticipate risk vectors, and craft policies that preempt unauthorized behavior. The process integrates with broader enterprise architecture, allowing automated provisioning, de-provisioning, and access adjustments that mirror organizational change. The result is a system capable of adapting dynamically to employee transitions, project shifts, and emergent business requirements.
Modern enterprises increasingly recognize that identity governance is not a static compliance exercise. It is a living discipline that evolves with organizational needs. By monitoring usage trends, detecting anomalies, and refining access hierarchies, professionals maintain an environment where productivity thrives without compromising security. This dynamic approach transforms identity management from a reactive necessity into a proactive enabler of strategic growth and operational resilience.
Automation as the Keystone of Efficient Access Management
Automation stands as a pivotal mechanism in contemporary identity management. Manual processes, often riddled with latency and human error, cannot scale to meet the demands of large, multifaceted organizations. Automated workflows empower enterprises to enforce policy adherence consistently while freeing administrative resources for strategic initiatives. Every provisioning request, role modification, or access revocation can be systematically executed based on pre-established rules, minimizing the risk of oversight and ensuring uniform application of governance principles.
In practice, automation encompasses far more than routine task execution. It integrates predictive analytics, contextual evaluation, and continuous monitoring to create a proactive identity ecosystem. By analyzing user behavior, system dependencies, and role interdependencies, automated systems can anticipate potential breaches or misalignments before they materialize. This foresight not only mitigates risk but also optimizes operational efficiency, ensuring that the right individuals possess the right access at the right time.
Furthermore, automation enhances organizational agility. Enterprises frequently undergo structural changes, mergers, or strategic pivots, each introducing complex access management challenges. Automated identity management frameworks adapt seamlessly to these changes, orchestrating updates across multiple systems without disrupting workflow continuity. By embedding intelligent policy logic and decision-making into automated processes, professionals reduce friction while maintaining robust governance. The result is a resilient system that supports organizational evolution without compromising control.
Integration Across Multisystem Environments
Organizations today operate within ecosystems of diverse applications, cloud services, and legacy infrastructure. Identity management cannot exist in isolation; it must integrate seamlessly across all touchpoints to ensure coherent governance. Integration is not merely technical—it is strategic, requiring professionals to understand system interdependencies, data flows, and operational priorities. By establishing a unified identity architecture, enterprises create a centralized governance model capable of enforcing policies consistently across disparate platforms.
The integration process entails harmonizing authentication protocols, aligning role hierarchies, and ensuring that access rights are coherent across systems. Professionals leverage single sign-on mechanisms, federated identity frameworks, and directory synchronization to reduce complexity while enhancing security. Such integration ensures that access modifications propagate automatically, reducing latency and eliminating inconsistencies that could otherwise expose vulnerabilities.
Integration also enhances visibility. Consolidated identity management provides a holistic view of who has access to what resources, under which conditions, and for how long. This visibility supports informed decision-making, precise auditing, and regulatory compliance. It transforms identity governance from a fragmented set of policies into a cohesive strategy that underpins enterprise security and operational efficiency.
Policy Enforcement as a Pillar of Compliance
Effective identity governance hinges upon meticulous policy enforcement. Policies dictate who can access which resources, under what circumstances, and with what privileges. Professionals meticulously define these parameters, ensuring that organizational objectives align with security imperatives and regulatory obligations. Enforcement is continuous, applying rules consistently and verifying adherence through automated checks, certification campaigns, and periodic audits.
Policy enforcement extends to dynamic contexts as well. Enterprises operate in environments where roles, responsibilities, and project scopes shift frequently. Professionals design adaptable policies that can accommodate these changes without compromising security. For instance, temporary project access can be granted automatically and revoked promptly upon completion, preventing lingering permissions that could lead to vulnerabilities.
Beyond internal compliance, policy enforcement fosters accountability and transparency. Detailed records of access decisions, role assignments, and approval workflows create a traceable audit trail. Organizations can demonstrate adherence to regulatory standards, internal controls, and best practices with precision. This traceability reinforces trust with stakeholders, reduces exposure to penalties, and underpins a culture of responsible data stewardship.
Continuous Monitoring and Proactive Risk Management
Identity governance does not conclude with policy implementation; it requires continuous monitoring to identify anomalies, anticipate threats, and refine access protocols. Modern identity management systems leverage real-time analytics to track user activity, detect deviations, and trigger alerts for suspicious behavior. By continuously observing patterns, organizations gain insights into emerging risks and operational inefficiencies.
Proactive monitoring supports predictive risk management. By analyzing historical data, usage trends, and system interdependencies, professionals can forecast potential vulnerabilities and take preemptive action. This forward-looking approach transforms identity governance from a reactive discipline into a strategic asset, mitigating risks before they manifest.
Continuous monitoring also fosters operational efficiency. By identifying redundant or outdated access rights, organizations can streamline roles, optimize workflows, and reduce administrative overhead. This ongoing refinement ensures that identity management remains aligned with organizational evolution, regulatory changes, and technological advancements. In essence, continuous monitoring establishes a feedback loop that strengthens security, enhances productivity, and reinforces governance integrity.
Sector-Specific Applications and Strategic Impact
The principles of identity governance manifest differently across sectors, reflecting each industry's unique operational demands. In financial services, precise control over access to sensitive client data is critical. Identity management systems automate approvals, synchronize accounts, and enforce strict segregation of duties. By integrating policy enforcement with real-time monitoring, banks mitigate fraud, enhance regulatory compliance, and accelerate client service delivery.
Healthcare organizations face complex challenges involving patient privacy, clinical workflows, and research data security. Professionals design workflows that ensure only authorized personnel access sensitive medical records while facilitating collaboration across multidisciplinary teams. Integration with electronic health records, secure delegation protocols, and periodic certification campaigns ensure patient data protection without hampering clinical efficiency.
In technology enterprises, rapid project cycles and dynamic team compositions create fluctuating access needs. Identity governance frameworks enable automated role adjustments, temporary project access grants, and timely revocation of privileges. Predictive analytics anticipate high-demand periods, ensuring uninterrupted access while maintaining robust control. The result is an environment where innovation and security coexist seamlessly.
Government agencies also derive significant benefits from sophisticated identity governance. Centralized management, standardized policies, and detailed auditing enhance transparency, accountability, and operational efficiency. Automated workflows streamline administrative processes, while continuous monitoring ensures compliance with regulatory frameworks and public accountability standards. These practices reinforce citizen trust and safeguard sensitive information across diverse departments.
Across these applications, common threads emerge: the fusion of automation, integration, policy enforcement, and continuous monitoring. Professionals harness identity governance expertise to deliver tailored solutions that balance efficiency, security, and compliance. This multifaceted impact underscores the strategic value of identity management as an enabler of organizational resilience and operational excellence.
Driving Innovation Through Identity Management
Identity governance extends beyond security and compliance to become a catalyst for innovation. By providing secure, seamless access, professionals enable employees, partners, and stakeholders to collaborate more effectively. Streamlined access management reduces friction, accelerates project delivery, and empowers decision-making with timely information.
Moreover, identity governance fuels data-driven insights. With visibility into access patterns, system utilization, and workflow bottlenecks, organizations can identify areas for optimization and innovation. Predictive analytics and intelligent automation transform raw data into actionable strategies, allowing enterprises to anticipate market shifts, optimize resource allocation, and enhance operational agility.
By embedding identity governance into the fabric of organizational strategy, enterprises unlock new possibilities for growth. Access becomes not merely a control mechanism but a strategic enabler that fosters innovation, collaboration, and resilience. Professionals who navigate this intersection of security, efficiency, and innovation provide organizations with a competitive advantage in an increasingly digital world.
The Evolution of Identity Management in the Digital Era
Identity management has transformed from a simple technical function into a central pillar of organizational strategy. In the early days of digital systems, managing user credentials and access rights was primarily a back-office operation, focused on efficiency and compliance. Today, identity management has become an active driver of security, operational resilience, and even business innovation. Organizations increasingly recognize that identity is not merely a gateway to systems but a crucial determinant of trust, accountability, and risk management. The rise of cloud computing, mobile platforms, and remote work has exponentially increased the complexity of identity ecosystems, making robust identity frameworks indispensable.
Modern identity management goes beyond controlling who can access what. It encompasses a spectrum of activities, including lifecycle management, continuous monitoring, behavioral analysis, and risk assessment. Enterprises are now required to safeguard sensitive data across distributed environments while providing seamless access for authorized personnel. This duality—ensuring security while maintaining operational fluidity—has created a demand for professionals who possess both technical expertise and strategic insight. Certified CA Identity Manager Professional expertise has emerged as a benchmark for individuals who can navigate this dynamic landscape, balancing governance, compliance, and technological innovation.
Organizations that adopt advanced identity management approaches experience profound benefits. Automated provisioning reduces human error, while real-time monitoring and analytics improve the detection of anomalies. Strategic identity frameworks can also enable data-driven decision-making, allowing executives to align security measures with broader business objectives. As technology continues to evolve, the centrality of identity management in protecting assets, facilitating collaboration, and maintaining competitive advantage cannot be overstated.
Artificial Intelligence and Machine Learning in Identity Governance
Artificial intelligence and machine learning have introduced a paradigm shift in identity governance. By leveraging sophisticated algorithms, AI can analyze user behavior, detect irregular access patterns, and identify potential security threats before they materialize. Unlike traditional systems, which rely on static rules and periodic audits, AI-driven frameworks offer predictive insights, enabling organizations to act proactively. For instance, deviations in login patterns or unusual access requests can trigger automated alerts or adaptive security measures, reducing the window of vulnerability.
Certified CA Identity Manager Professional methodologies emphasize integrating these intelligent systems into governance frameworks without compromising control or auditability. The focus is not merely on automation but on informed automation, where AI enhances human decision-making rather than replacing it. Machine learning models can continuously refine their predictions based on historical data, allowing organizations to dynamically adjust policies, optimize workflows, and strengthen security protocols. This combination of predictive intelligence and policy enforcement creates a resilient identity ecosystem capable of adapting to emerging threats.
Moreover, AI facilitates enhanced user experiences. Intelligent identity systems can reduce friction in authentication processes by employing context-aware mechanisms, such as adaptive multi-factor authentication, behavioral biometrics, and risk-based access controls. These solutions maintain high security standards while minimizing interruptions to productivity. Organizations that harness AI in identity management gain a competitive edge by blending efficiency, compliance, and security into a cohesive operational model.
Implementing Zero Trust Architectures
The concept of zero trust has revolutionized how organizations approach security. Traditional perimeter-based models assumed that internal networks were inherently trustworthy, leaving systems vulnerable to insider threats and lateral attacks. Zero trust, by contrast, operates on the principle that no user or device should be trusted by default. Access is continuously validated, and authentication is enforced at every interaction.
Identity management sits at the heart of zero trust architectures. Professionals trained in Certified CA Identity Manager Professional frameworks are adept at defining granular access policies, implementing dynamic authentication mechanisms, and monitoring user activity across hybrid and cloud environments. This ensures that security extends beyond conventional boundaries and adapts to modern organizational structures, which often include remote employees, third-party vendors, and complex application ecosystems.
Zero trust also encourages continuous monitoring and risk assessment. By employing analytics and AI-driven insights, organizations can detect subtle deviations in user behavior, adjust access privileges dynamically, and mitigate threats in real-time. Such capabilities are critical in an era where cyberattacks are increasingly sophisticated and rapid response is essential. By embedding zero trust principles into identity governance, organizations achieve not only heightened security but also operational agility, enabling secure collaboration across distributed teams and digital platforms.
Decentralized Identity and Blockchain Innovations
Decentralized identity frameworks are redefining the traditional paradigms of identity management. Rather than relying solely on centralized directories or authoritative databases, decentralized models distribute control and verification across secure, blockchain-based networks. This shift enhances privacy, reduces dependency on single points of failure, and empowers users with greater control over their personal information.
Certified CA Identity Manager Professional expertise is instrumental in navigating these emerging paradigms. Professionals are trained to integrate decentralized identity solutions with existing governance and compliance structures, ensuring continuity, security, and operational coherence. Blockchain technology provides immutable records of identity transactions, enabling auditability while preserving privacy through cryptographic protocols. These frameworks support innovative applications such as self-sovereign identity, secure digital credentials, and cross-organizational authentication.
Organizations adopting decentralized identity systems can reduce friction in access management, simplify compliance processes, and enhance trust among users and partners. The transparency and security inherent in blockchain-based authentication align with the broader objectives of modern identity management: safeguarding assets, promoting usability, and supporting strategic decision-making. By embracing decentralized innovations, enterprises position themselves at the forefront of technological evolution while reinforcing their security posture.
Strategic Leadership in Identity Governance
While technological advancements are critical, effective identity management also depends on strategic leadership. Professionals equipped with Certified CA Identity Manager Professional knowledge play a pivotal role in guiding organizations toward integrated, future-ready solutions. They bridge the gap between technical implementation and business strategy, ensuring that identity governance initiatives align with regulatory requirements, operational goals, and risk management frameworks.
Strategic leadership involves advocating for investments in automation, advanced analytics, and security enhancements. It also requires balancing cost, usability, and efficiency to ensure that identity systems contribute positively to organizational performance. Professionals must communicate the value of identity governance to executive decision-makers, demonstrating how it safeguards critical assets while enabling collaboration, productivity, and innovation. By combining technical expertise with strategic insight, these leaders ensure that identity management evolves from a purely operational task into a competitive advantage.
Additionally, leadership extends to change management and user engagement. Implementing sophisticated identity frameworks often necessitates cultural and procedural shifts. Professionals guide teams in adopting new workflows, embracing automated provisioning, and adhering to security policies without compromising productivity. Such guidance fosters a culture of accountability, security consciousness, and innovation, amplifying the long-term impact of identity management initiatives.
Enhancing Operational Efficiency through Identity Automation
Automation is a cornerstone of modern identity management. Organizations face an ever-expanding volume of access requests, policy updates, and compliance audits, making manual processes increasingly impractical. Automated identity workflows streamline these tasks, reduce human error, and accelerate response times. By reducing the reliance on manual intervention, organizations achieve not only speed but also greater consistency in enforcing identity policies. Repetitive tasks, which once consumed valuable administrative hours, are now handled reliably by automated sequences, freeing professionals to focus on strategic decision-making rather than routine maintenance.
Certified CA Identity Manager Professional methodologies provide comprehensive frameworks for designing, implementing, and optimizing automation in identity governance. These methodologies emphasize aligning automation with organizational priorities, ensuring that workflows do not merely replicate existing inefficiencies but actively enhance operational capacity. Automated provisioning and de-provisioning of accounts are particularly impactful, ensuring that users gain immediate access to necessary resources while simultaneously reducing the risk of orphaned accounts or unauthorized access. When a user joins, moves within, or leaves an organization, the system automatically adjusts their privileges in accordance with defined roles and policies, eliminating delays that could otherwise hinder productivity or compromise security.
Policy enforcement is another area where automation delivers measurable benefits. Manual policy reviews are labor-intensive and prone to oversight, whereas automated systems continuously apply predefined rules, evaluate contextual risk factors, and adjust access dynamically. For example, permissions can be temporarily escalated for critical projects and automatically reverted when no longer required. This dynamic adaptability ensures that the principle of least privilege is upheld consistently, protecting sensitive resources without imposing unnecessary friction on legitimate work. By embedding intelligence into these workflows, organizations achieve a balance where security measures enhance rather than obstruct business operations.
Automation extends beyond simple task execution into predictive and analytical realms. Advanced identity systems leverage machine learning and predictive analytics to identify usage patterns, anticipate workflow bottlenecks, and recommend process improvements before issues arise. By monitoring user activity, access frequency, and compliance trends, organizations gain actionable insights that inform both immediate decisions and long-term strategy. These insights help prioritize which workflows to automate first, allocate resources more effectively, and forecast future system demands with greater precision. Predictive capabilities transform identity management from a reactive discipline into a proactive, intelligence-driven practice.
Operational efficiency is further reinforced through the integration of AI-driven insights into identity workflows. AI engines can detect anomalies, such as unusual access patterns or deviations from standard approval timelines, and initiate corrective measures automatically. This reduces the need for manual intervention while maintaining vigilance against potential security threats. Continuous monitoring ensures that system performance and compliance remain aligned with organizational objectives. Alerts and automated responses can be configured to escalate only when truly necessary, reducing alert fatigue and allowing human expertise to focus where it has the most strategic impact.
The benefits of identity automation extend into workforce productivity as well. Employees no longer face delays waiting for access approvals or policy clarifications. Self-service portals enable users to request access, reset credentials, or manage their permissions with minimal friction. These portals, backed by automated workflows, maintain full compliance and oversight while enhancing user satisfaction. The reduction in administrative delays fosters a more agile operational environment where tasks are completed promptly, collaboration is smoother, and project timelines are accelerated.
Furthermore, automation supports scalability. As organizations grow, the volume of identity-related requests multiplies, often exponentially. Manual processes cannot keep pace with such growth, leading to delays, errors, and potential security gaps. Automated identity systems, however, handle expansion effortlessly, adjusting workflows, provisioning new accounts, and enforcing policies across increasingly complex infrastructures. This scalability ensures that organizational growth does not compromise security, compliance, or operational efficiency.
Ultimately, identity automation is more than a technological enhancement; it represents a strategic enabler. By integrating automated workflows with predictive analytics, AI-driven monitoring, and dynamic policy enforcement, organizations create a resilient, responsive environment where security, compliance, and productivity coexist seamlessly. Routine administrative burdens are minimized, user satisfaction is elevated, and professionals can redirect their focus toward innovation, risk mitigation, and strategic growth initiatives. Automation transforms identity management from a labor-intensive obligation into a dynamic operational advantage, fostering a culture of efficiency, reliability, and forward-looking adaptability.
The Future of Identity Management
The trajectory of identity management points toward greater integration, intelligence, and strategic relevance. Emerging technologies such as AI, blockchain, and zero trust architectures will continue to reshape the landscape, demanding adaptive, forward-thinking professionals. Certified CA Identity Manager Professional expertise equips individuals to navigate this evolving environment, combining technical skill with strategic acumen to drive organizational resilience.
Future identity systems will emphasize context-aware authentication, adaptive policy enforcement, and seamless user experiences. Risk-based frameworks will become standard, enabling organizations to dynamically balance access, security, and compliance. Decentralized identity models will empower users while simplifying governance, and automation will handle routine processes, freeing human expertise for strategic decision-making.
Organizations that invest in these principles will benefit from a secure, efficient, and scalable identity ecosystem. Identity management will no longer be a back-office function but a central enabler of operational excellence, competitive advantage, and innovation. Professionals who master these techniques will lead organizations in leveraging identity as both a protective measure and a strategic asset, shaping the digital future with foresight, intelligence, and resilience.
Conclusion
The journey through identity management, from foundational concepts to advanced strategies and emerging innovations, highlights the critical role of expertise in Certified CA Identity Manager Professional practices. Organizations today operate in a complex digital ecosystem where user identities, access permissions, and security compliance are intertwined. Professionals trained in these principles bridge the gap between technical implementation and strategic oversight, ensuring that systems are not only secure but also efficient, scalable, and adaptable.
Across industries, the impact of robust identity management is clear. Automation reduces manual errors, lifecycle management ensures appropriate access throughout an employee’s tenure, and predictive analytics provide proactive risk mitigation. Troubleshooting and optimization maintain system reliability, while real-world applications demonstrate measurable benefits in operational efficiency and compliance. As technology evolves, innovations such as artificial intelligence, zero trust frameworks, and decentralized identity models further expand the potential of identity governance.
Ultimately, mastering Certified CA Identity Manager Professional principles equips professionals to design, implement, and sustain identity management ecosystems that serve both organizational needs and regulatory obligations. By combining technical skill with strategic insight, organizations can confidently safeguard their digital assets, streamline operations, and embrace the opportunities of a dynamic, digitally-driven future. Identity management is no longer just a support function—it is a cornerstone of secure, efficient, and forward-looking enterprises.
Frequently Asked Questions
How does your testing engine works?
Once download and installed on your PC, you can practise test questions, review your questions & answers using two different options 'practice exam' and 'virtual exam'. Virtual Exam - test yourself with exam questions with a time limit, as if you are taking exams in the Prometric or VUE testing centre. Practice exam - review exam questions one by one, see correct answers and explanations).
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Pass4sure products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Pass4sure software on?
You can download the Pass4sure products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email sales@pass4sure.com if you need to use more than 5 (five) computers.
What are the system requirements?
Minimum System Requirements:
- Windows XP or newer operating system
- Java Version 8 or newer
- 1+ GHz processor
- 1 GB Ram
- 50 MB available hard disk typically (products may vary)
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.