Exam Code: 1D0-571
Exam Name: CIW v5 Security Essentials
Certification Provider: CIW
Corresponding Certifications: CIW, CIW Web Security Associate, CIW Web Security Professional
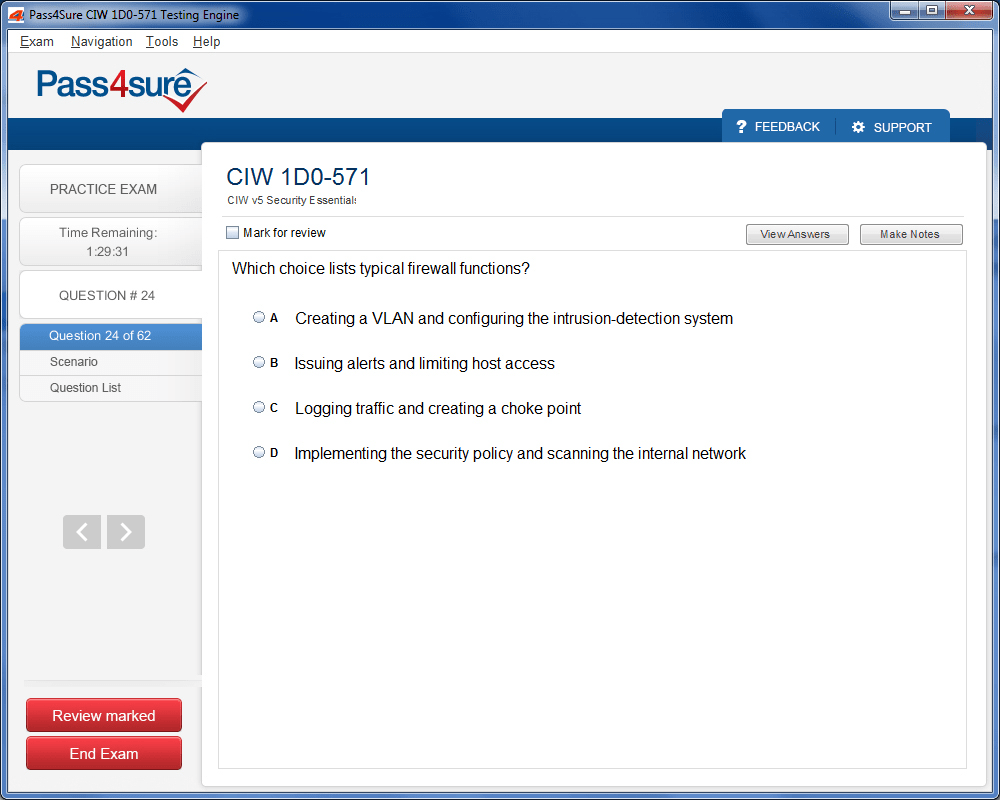
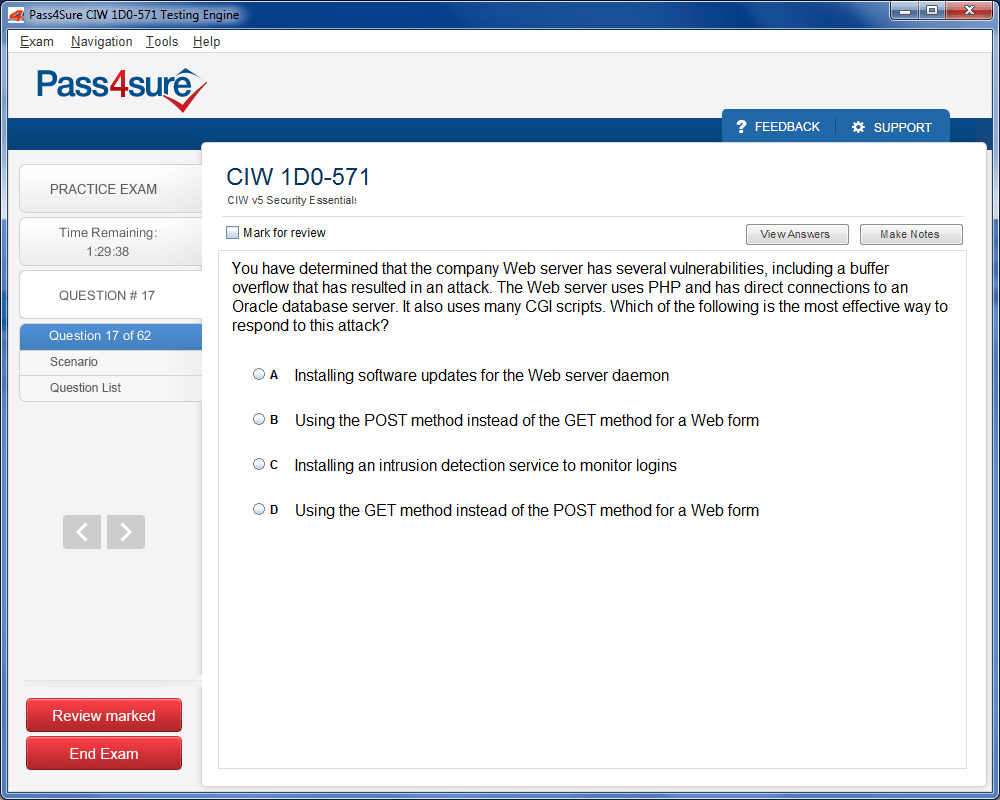
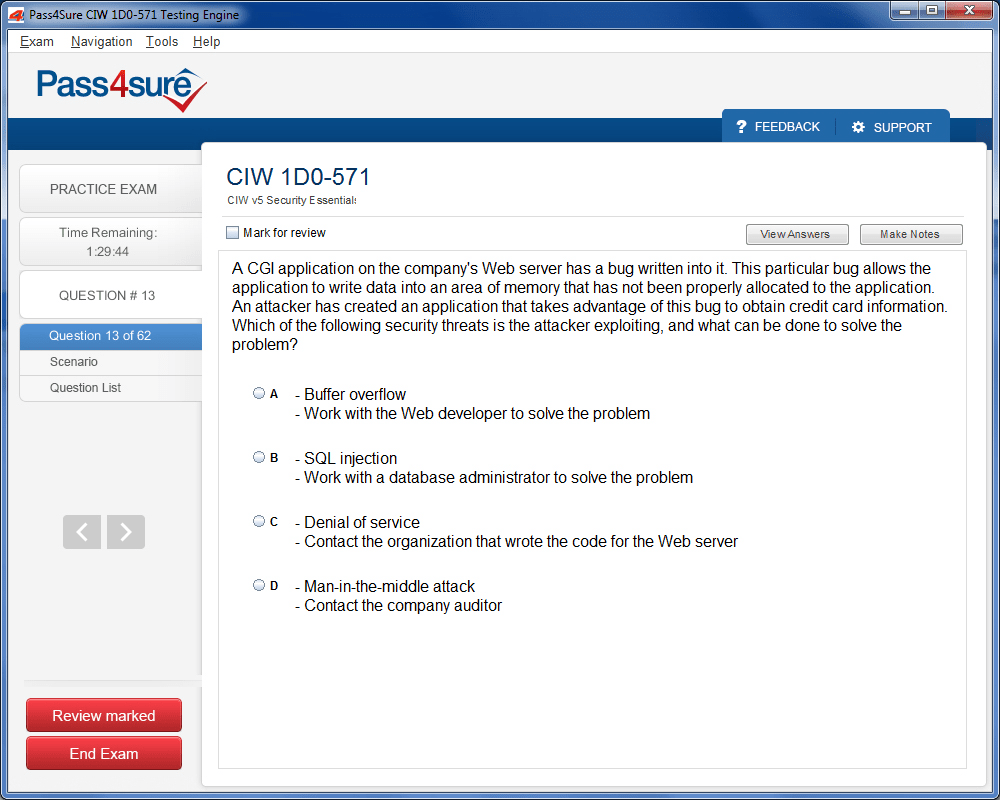
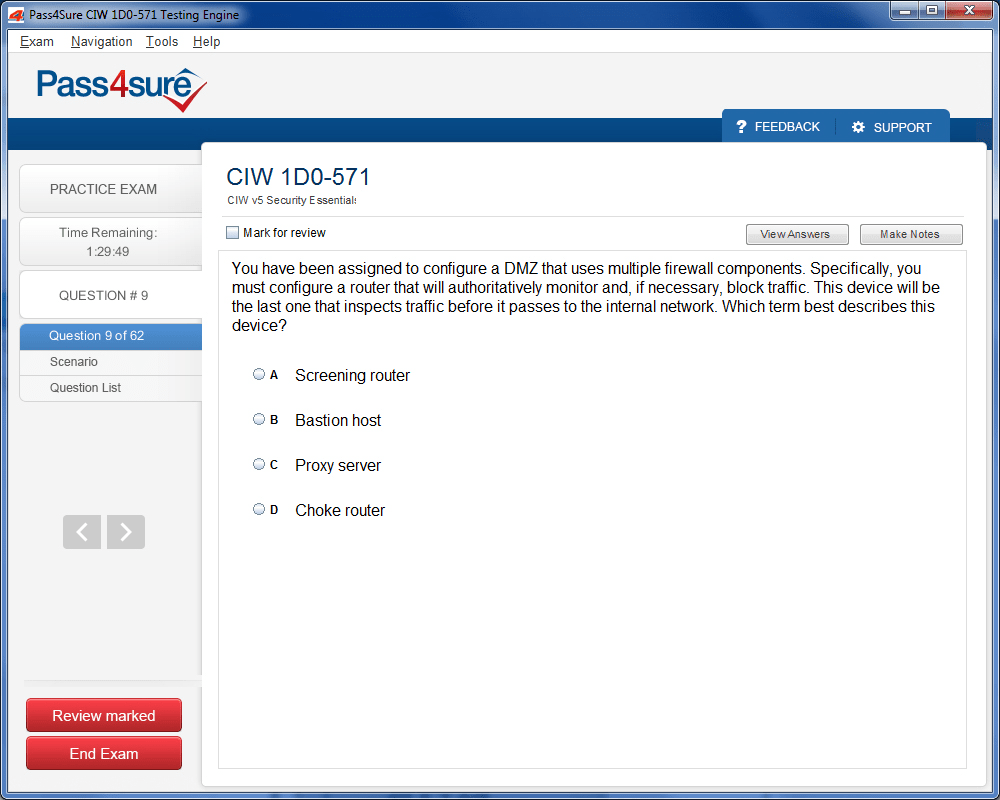
1D0-571 Exam Product Screenshots
Product Reviews
Strengthen Your Resolve
"Only by proper preparation, perseverance, and dedication, can one hope to succeed. Pass4sure gave me the opportunity to hone these attributes so as to attain glory in my 1D0-571 certification exam. They have assembled a complete and valuable package in their 1D0-571 CIW Web Security Associate preparatory resources to help candidates excel in their test. Not only did I clear the exam, but I also earned a respectful position in the eyes of my peers. I owe a lot to Pass4sure for their exquisite Certifications 1D0-571 preparatory materials.
Daniel Quentin"
Frequently Asked Questions
How does your testing engine works?
Once download and installed on your PC, you can practise test questions, review your questions & answers using two different options 'practice exam' and 'virtual exam'. Virtual Exam - test yourself with exam questions with a time limit, as if you are taking exams in the Prometric or VUE testing centre. Practice exam - review exam questions one by one, see correct answers and explanations.
How can I get the products after purchase?
All products are available for download immediately from your Member's Area. Once you have made the payment, you will be transferred to Member's Area where you can login and download the products you have purchased to your computer.
How long can I use my product? Will it be valid forever?
Pass4sure products have a validity of 90 days from the date of purchase. This means that any updates to the products, including but not limited to new questions, or updates and changes by our editing team, will be automatically downloaded on to computer to make sure that you get latest exam prep materials during those 90 days.
Can I renew my product if when it's expired?
Yes, when the 90 days of your product validity are over, you have the option of renewing your expired products with a 30% discount. This can be done in your Member's Area.
Please note that you will not be able to use the product after it has expired if you don't renew it.
How often are the questions updated?
We always try to provide the latest pool of questions, Updates in the questions depend on the changes in actual pool of questions by different vendors. As soon as we know about the change in the exam question pool we try our best to update the products as fast as possible.
How many computers I can download Pass4sure software on?
You can download the Pass4sure products on the maximum number of 2 (two) computers or devices. If you need to use the software on more than two machines, you can purchase this option separately. Please email sales@pass4sure.com if you need to use more than 5 (five) computers.
What are the system requirements?
Minimum System Requirements:
- Windows XP or newer operating system
- Java Version 8 or newer
- 1+ GHz processor
- 1 GB Ram
- 50 MB available hard disk typically (products may vary)
What operating systems are supported by your Testing Engine software?
Our testing engine is supported by Windows. Andriod and IOS software is currently under development.
1D0-571 CIW Exam Prep: Step into a Successful Web Security Career
As humanity delves deeper into the digital frontier, our dependency on interconnected systems has grown exponentially. From financial transactions to government infrastructure, and from healthcare databases to personal communications, the web has become a vast ecosystem supporting nearly every human endeavor. Yet, this growth has invited perilous shadows. Malicious actors, driven by motives ranging from financial gain to political sabotage, infiltrate vulnerable systems with ever-evolving strategies. Against this turbulent backdrop, the mastery of cybersecurity emerges not merely as a professional skill but as an essential societal safeguard. The CIW Web Security Associate certification, identified by exam code 1D0-571, arises as a pivotal credential, preparing individuals to protect, defend, and fortify digital landscapes against encroaching threats.
Exam Code 1D0-571: The Formal Gateway to Certification
The CIW Web Security Associate certification is formalized through the 1D0-571 exam, a structured assessment designed to gauge both theoretical knowledge and practical acumen in web security. This exam is 90 minutes long and composed of 62 carefully curated questions. The passing threshold is set at 76%, a deliberate standard that ensures only those with genuine comprehension and application skills succeed. Unlike many simplistic examinations that emphasize memorization, this exam demands reasoning under pressure. Every question, whether about access control, encryption methods, or network vulnerabilities, requires the candidate to demonstrate an ability to translate abstract knowledge into practical solutions. Thus, the exam code 1D0-571 serves as the official marker of readiness, separating those who merely study cybersecurity from those prepared to practice it.
Foundations That Precede the Journey
Although the certification provides a foundational framework, it does not begin in a vacuum. Candidates embarking on the 1D0-571 journey are expected to possess certain preliminary skills. Familiarity with basic networking, a grasp of internet architecture, and exposure to fundamental web technologies create the scaffolding upon which the certification content is constructed. Without this scaffolding, the more complex discussions on packet filtering, intrusion detection, or secure authentication may collapse into confusion. Meeting the prerequisites ensures smoother progression through the syllabus and allows aspirants to devote their energies entirely to the intricacies of security.
Dissecting the Syllabus with Precision
The syllabus of the CIW Web Security Associate exam, codified in 1D0-571, stretches across diverse yet interwoven topics. It includes principles of network security, encryption strategies, access control mechanisms, authentication systems, firewalls, and risk management frameworks. Additionally, candidates must explore methods for secure e-commerce, incident response strategies, and the nuances of malicious software. This sweeping scope reflects the reality of web security—threats are not confined to a single domain but weave across multiple layers of interaction. By dividing the syllabus into smaller, digestible modules, candidates can tackle each domain methodically, ensuring holistic mastery without neglecting essential subsections.
The Anatomy of Effective Study Plans
Preparation for the 1D0-571 exam is less about cramming volumes of material and more about a disciplined strategy. The human mind retains knowledge best through consistent, structured learning. Allocating two hours per day over a span of weeks provides balance, avoiding both exhaustion and superficiality. This method allows for revisiting complex ideas, strengthening retention through repetition. Creating a study calendar, wherein each week is devoted to a theme—cryptography, firewalls, malware defense—ensures gradual but comprehensive coverage. Such incremental advancement fosters confidence while preventing the overwhelming sensation that often accompanies broad syllabi.
Harnessing the Power of Practice Questions
Sample questions are indispensable allies in exam preparation. They allow candidates to measure their understanding against real-world scenarios, sharpening their analytical reflexes. A candidate may know that AES is a robust encryption standard, but only through practice questions do they learn when and why AES should be chosen over alternatives in a specific context. Furthermore, exposure to practice questions reduces exam-day anxiety by familiarizing learners with the phrasing, complexity, and logic of actual exam problems. Confidence is not a fleeting emotion but a cultivated trait, grown through repeated encounters with uncertainty until it becomes second nature.
Psychological Readiness and Human Wellness
The journey toward certification is as much psychological as it is intellectual. Prolonged stress, fatigue, or imbalance can sabotage even the most diligent learners. Preparing for the 1D0-571 exam demands not just intellectual rigor but mindful attention to health and wellness. Adequate sleep sharpens cognitive performance, nutritious food sustains energy, and brief, intentional breaks reset mental focus. Anxiety management techniques—such as deep breathing, visualization, or meditation—serve as subtle yet powerful tools. A calm, composed candidate interprets questions more clearly and makes sharper decisions than one clouded by nerves. The mental dimension of preparation is therefore an inseparable component of success.
Professional Leverage in Competitive Markets
Achieving the CIW Web Security Associate certification through exam 1D0-571 endows candidates with more than personal satisfaction; it grants tangible professional leverage. Employers in a saturated job market seek demonstrable proof of competency, and this certification provides exactly that. For those aspiring to launch a career in cybersecurity, the credential acts as a passport to entry-level positions. For professionals already embedded in IT, it enriches their portfolios, marking them as multidimensional experts capable of integrating security into broader technological landscapes. The certification is not an endpoint but a springboard to advanced credentials and more specialized career pathways.
Ethical Dimensions of Cybersecurity Knowledge
Beyond technical expertise lies an ethical responsibility. Those who earn the CIW Web Security Associate certification must recognize the power of their knowledge. Techniques used to defend networks can, in the wrong hands, be twisted into methods of exploitation. Thus, integrity and moral clarity are as vital as technical mastery. Certified individuals are guardians of digital trust, entrusted with preserving confidentiality, protecting data, and ensuring the integrity of online transactions. Ethics in cybersecurity is not ornamental—it is the foundation of responsible practice.
Global Applicability of Skills Earned
The 1D0-571 exam does not prepare candidates for localized challenges alone. The concepts transcend geographic boundaries, equipping professionals to operate in multinational contexts. An e-commerce platform in Asia faces the same threats of SQL injection as one in Europe, and phishing scams exploit human psychology across cultures. This universality of security principles underscores the global value of the certification. For professionals with ambitions beyond their immediate environment, this international relevance opens doors to opportunities worldwide.
Integrating Study with Practical Experience
While theoretical study forms the backbone of preparation, practical application breathes life into the learning process. Candidates should complement their studies by experimenting with firewalls, encryption tools, and network monitoring software. Conducting small-scale vulnerability assessments or simulating phishing defense exercises transforms passive knowledge into an active skill. This experiential learning ensures that certification holders are not mere test-takers but capable practitioners ready for real-world deployment.
The Shifting Terrain of Cyber Threats
The dynamism of cybersecurity distinguishes it from many other disciplines. A technique considered secure today may be obsolete tomorrow. From ransomware that paralyzes cities to state-sponsored cyber espionage, threats continuously mutate. The CIW Web Security Associate certification prepares candidates not just with static knowledge but with an adaptive mindset—an awareness that vigilance is perpetual. This adaptability ensures that certified professionals are not blindsided by change but remain agile defenders of digital systems.
Synergy Across IT Domains
Knowledge gained through the 1D0-571 exam synergizes with other IT domains. Developers become adept at writing secure code, network engineers gain sharper insights into intrusion detection, and system administrators enforce stronger access policies. This cross-pollination of knowledge elevates organizational resilience, as every role contributes to a collective culture of security. The certification thus does not exist in isolation but interlocks with broader technological expertise, strengthening the overall digital fabric.
The Role of Community and Collaborative Learning
Preparation is enhanced by collaboration. Study groups and peer discussions encourage candidates to articulate their understanding, often revealing gaps they may have overlooked. Explaining encryption to a peer, for example, not only solidifies one’s own comprehension but also sharpens the ability to convey complex ideas clearly—an essential skill in professional contexts. Communities, whether physical or virtual, provide encouragement, motivation, and diverse perspectives, transforming solitary preparation into collective growth.
Building Exam-Day Confidence
As exam day approaches, confidence must be meticulously cultivated. Mock exams under timed conditions replicate the real testing environment, teaching candidates how to allocate minutes wisely and avoid panic. Visualization techniques, where candidates imagine themselves succeeding, can profoundly shift mental states. By the time they sit for the 1D0-571 exam, successful candidates are not wide-eyed novices but steady professionals, ready to showcase skills honed through rigorous preparation. Confidence becomes both shield and sword, guiding them to triumph.
Lifelong Learning Beyond Certification
While the 1D0-571 exam provides a formal conclusion to the certification journey, true mastery extends far beyond. Cybersecurity professionals must commit to lifelong learning, staying abreast of new vulnerabilities, technologies, and defense strategies. The certification serves as a foundation stone, but the edifice of expertise must be built continuously. Those who adopt this mindset not only protect systems but also future-proof their own careers in a domain that evolves as swiftly as the threats it counters.
Smart Preparation Strategies for the 1D0-571 Exam
Cracking the CIW Web Security Associate exam is less about sheer intensity and more about strategy, foresight, and efficient use of mental resources. Many candidates rush headlong into textbooks or dense study guides, only to find themselves exhausted or overwhelmed halfway through their preparation. Smart preparation involves creating a system that balances comprehension, repetition, and focus with time management and well-being. It is a holistic journey, not just an intellectual race.
The exam tests one’s ability to understand principles of web security, authentication protocols, intrusion detection, and encryption mechanisms. While the topics themselves are complex, the real challenge lies in navigating them with clarity and resilience. A candidate who designs a structured study plan and implements effective methods will not only absorb knowledge more efficiently but also cultivate confidence to handle the exam with calm determination. Smart preparation is essentially about mastering the art of consistency, creating a rhythm of study that aligns with both learning styles and personal circumstances.
A first step in intelligent preparation is crafting a timetable that reflects reality rather than fantasy. Too often, learners design ambitious plans that demand six or seven hours of study daily, only to abandon them after a week due to burnout. A smarter approach is to allocate one to two hours per day, segmented into manageable intervals. For example, forty-five minutes of focused study followed by a fifteen-minute break can drastically improve retention. These short breaks allow the brain to recharge and prevent information overload. Over weeks, such a plan ensures a steady accumulation of knowledge without creating fatigue or frustration.
Taking notes is another underrated but vital tactic. The simple act of writing forces the brain to engage deeply with material, distilling complex information into concise, digestible points. For example, while studying encryption algorithms, one might jot down the difference between symmetric and asymmetric encryption in a few lines. Similarly, when reviewing access control mechanisms, summarizing them into categories like mandatory, discretionary, and role-based provides clarity. These notes later serve as a quick reference, particularly useful for rapid revision in the days leading up to the exam. Beyond mere summarization, note-taking sharpens analytical thinking, allowing the learner to grasp how different concepts interconnect.
Equally important is choosing the right study materials. In today’s information-saturated world, candidates are bombarded with countless resources, from bulky textbooks to scattered online tutorials. The danger lies in scattering attention across too many platforms. The key to smart preparation is selectivity—focusing on high-quality guides, concise PDFs, and practice question sets that mirror the exam’s style. Regular practice tests not only familiarize candidates with the question format but also act as diagnostic tools. By identifying weak areas, they help in directing energy where it is most needed. Importantly, candidates should not be discouraged by initial low scores; instead, they should view these results as stepping stones in a long-term improvement process.
Repetition is the glue that binds knowledge into memory. Complex subjects such as intrusion detection systems, firewall architecture, and secure session management cannot be mastered in a single reading. Revisiting these topics multiple times gradually deepens understanding. A concept that feels confusing on the first encounter often becomes clearer upon the second or third review. Moreover, integrating real-world scenarios into study sessions makes learning more dynamic. For instance, instead of merely memorizing definitions of authentication methods, a learner might reflect on how multifactor authentication is applied in online banking. Such contextualization bridges the gap between theory and practice, reinforcing comprehension.
Time management is another cornerstone of smart preparation. It applies both to the preparation phase and to the exam itself. During the study, setting timers for practice tests ensures that candidates become accustomed to thinking within time constraints. This practice sharpens focus and prevents the tendency to dwell too long on a single problem. On exam day, effective pacing is critical. Candidates who manage their time wisely can attempt every question without succumbing to last-minute panic. The best strategy is to answer familiar questions quickly, mark the more difficult ones for later, and revisit them with any remaining time.
Adaptability is an attribute that distinguishes successful candidates from those who falter. If a certain method proves ineffective, it is essential to pivot without hesitation. For example, if passive reading fails to yield results, switching to active techniques such as creating flashcards, drawing mind maps, or teaching concepts aloud can refresh engagement. Visual learners may benefit from diagrams illustrating network layers, while auditory learners might record themselves explaining topics for playback during commutes. Flexibility ensures that preparation remains dynamic rather than stagnant.
The study environment itself plays a crucial role. A cluttered desk, noisy surroundings, or constant distractions can sabotage even the most diligent efforts. Establishing a quiet, organized study space signals the brain to enter a focused state. Removing unnecessary digital distractions, such as silencing notifications, helps preserve concentration. Candidates who treat their study environment with intentionality find themselves naturally more disciplined. Additionally, weaving in moments of physical movement—simple stretches or short walks—refreshes energy and maintains alertness across long preparation periods.
Self-assessment should form a recurring loop throughout preparation. Simply studying without evaluation risks building a false sense of confidence. At regular intervals, candidates should pause to test themselves on key topics and analyze their progress. Keeping a record of strengths and weaknesses allows for strategic adjustment of study plans. For instance, someone excelling in cryptography but struggling with threat mitigation should allocate more time to the weaker area. This targeted focus ensures a balanced proficiency across all exam domains.
Equally significant is the role of mental resilience. Anxiety, if left unchecked, can cripple performance. Smart preparation includes nurturing emotional stability through mindfulness practices, controlled breathing, or even short meditative exercises. Such techniques quiet the mind, sharpen focus, and reduce pre-exam jitters. A calm and composed candidate is more likely to recall knowledge accurately under pressure than one overwhelmed by panic. Cultivating mental composure alongside intellectual mastery completes the holistic preparation cycle.
Another layer of effective preparation involves community and collaboration. Studying in isolation can sometimes limit exposure to new perspectives. Forming or joining study groups allows candidates to exchange insights, test each other’s understanding, and share practical tips. Explaining a concept to a peer often reveals gaps in one’s own knowledge, which can then be reinforced. Collaboration also adds motivation, as accountability within a group reduces the temptation to procrastinate.
In addition, integrating digital tools wisely can enhance efficiency. Applications that create flashcards, track study progress, or set reminders for revision sessions streamline the preparation process. However, digital resources should be used purposefully rather than becoming another source of distraction. When employed judiciously, technology transforms preparation into an organized and measurable endeavor, ensuring that every session contributes to progress.
Nutrition, rest, and physical well-being also intertwine with academic performance. A tired mind struggles to absorb and recall information, while poor dietary habits can reduce concentration. Candidates should prioritize sleep, balanced meals, and hydration throughout the preparation period. Exercise, even light daily activity, increases oxygen flow to the brain and sharpens alertness. In this sense, exam preparation transcends academics; it becomes a lifestyle adjustment where physical health supports cognitive function.
Visualization is another powerful yet often overlooked technique. Imagining oneself sitting in the exam hall, reading questions calmly, and answering with confidence primes the mind for success. This mental rehearsal reduces fear of the unknown and instills a sense of familiarity. Many high-performing candidates employ visualization as a supplement to study, strengthening both confidence and composure.
Finally, consistency reigns supreme in the realm of exam preparation. Sporadic bursts of intense study are less effective than a steady, disciplined approach. Each day of preparation, even if brief, adds another layer to the foundation of knowledge. Over time, these incremental efforts culminate in readiness. The candidate who studies an hour daily for several months often outperforms the one who crams frantically in the final weeks. The key is to sustain momentum, to view preparation as a marathon rather than a sprint.
When these strategies coalesce—structured planning, selective resources, active engagement, repetition, time management, adaptability, conducive environment, self-assessment, resilience, collaboration, digital optimization, physical well-being, visualization, and consistency—they create a holistic framework for success. The CIW Web Security Associate exam ceases to be an intimidating obstacle and instead becomes a navigable challenge. The candidate emerges not only prepared for the exam but also equipped with habits of discipline, adaptability, and clarity that extend far beyond the test itself.
Network Security Fundamentals
A cornerstone of the CIW 1D0-571 syllabus is its thorough exploration of network security fundamentals. This segment guides candidates through the essential framework of safeguarding digital communication channels. It emphasizes the necessity of secure network architecture, where layers of defense intertwine to reduce vulnerabilities. Within this scope, candidates encounter the mechanics of firewalls, devices that regulate inbound and outbound traffic with precision, forming the first line of protection against unauthorized access. Equally important are intrusion detection and prevention systems, which serve as vigilant sentinels, constantly monitoring for anomalous patterns that could signify malevolent intrusion attempts. Understanding how these systems interact within a cohesive design equips individuals to construct resilient network environments.
Another crucial point in this domain is the design of secure networks themselves. Rather than simply deploying isolated components, the syllabus highlights how thoughtful design principles strengthen overall infrastructure. Concepts like segmentation, demilitarized zones, and layered defenses ensure that even if one barrier falters, others remain intact to protect sensitive systems. Candidates gain clarity on why secure network design is less about assembling individual tools and more about orchestrating them harmoniously.
Data Protection and Encryption
In an era dominated by the relentless exchange of digital information, data protection assumes a role of paramount importance. The syllabus dedicates significant attention to ensuring that information retains both its integrity and confidentiality throughout its lifecycle. Encryption, the art of converting readable data into an indecipherable format for unauthorized entities, is central here. Candidates must acquaint themselves with symmetric and asymmetric algorithms, understanding when each type delivers maximum effectiveness.
The protocols that guarantee secure transmission, such as SSL and TLS, are examined in depth. These tools shield sensitive exchanges like financial transactions or login credentials from interception. Grasping how encryption pairs with hashing mechanisms strengthens the ability to confirm authenticity and prevent tampering. Furthermore, the syllabus underscores how secure communication extends beyond technology, encouraging the implementation of consistent organizational practices that prioritize confidentiality. Mastery of these elements transforms abstract technical concepts into tangible protective measures within professional practice.
Authentication and Access Control
The safeguarding of digital environments demands more than barriers; it requires the careful regulation of who may enter. The syllabus delves into authentication and access control, two intertwined elements of security architecture. Candidates explore the nuances of authentication systems that confirm user identities, from basic password mechanisms to advanced multi-factor methods integrating biometrics, tokens, or one-time codes.
Password policies form another essential theme. Candidates learn why strong, unique, and frequently updated credentials deter unauthorized exploitation. Beyond authentication lies the realm of access control, where users are assigned specific permissions based on their roles or responsibilities. The syllabus introduces role-based access control as a practical model that ensures individuals only access what they legitimately require. This prevents unnecessary exposure of critical systems and reduces the risk of internal compromise. By internalizing these principles, candidates acquire the ability to create environments where security and usability coexist in balance.
Understanding Web Threats and Vulnerabilities
Another compelling dimension of the syllabus focuses on the threats that lurk within digital landscapes. To secure effectively, one must first understand the enemy. Candidates study common vulnerabilities, including SQL injection, which manipulates database queries; cross-site scripting, which exploits trust between users and websites; and phishing, which deceives individuals into revealing sensitive data.
By analyzing these methods, learners recognize the psychological and technical tactics employed by adversaries. Such awareness sharpens defensive strategies, allowing proactive anticipation rather than reactive response. The syllabus does not treat these topics as abstract risks but as everyday challenges that professionals must navigate in dynamic web environments. Understanding vulnerabilities becomes a form of empowerment, giving candidates the foresight to predict, prevent, and neutralize malicious campaigns before they escalate.
Risk Management Principles
No syllabus on security could be complete without a strong emphasis on risk management. Within the CIW 1D0-571 framework, candidates are introduced to the systematic identification, analysis, and prioritization of risks. This involves measuring the probability of threats, evaluating their potential impact, and deciding which mitigation measures are most cost-effective.
Risk assessment is complemented by the exploration of frameworks that aid organizations in structuring their security posture. The syllabus instills the principle that not all risks can be eliminated, but they can be managed with foresight and proportional control. Candidates learn to weigh operational needs against protective measures, ensuring that security does not stifle functionality. Such strategic thinking elevates preparation from technical memorization to real-world application, aligning theory with professional practicality.
Incident Response and Recovery
Despite the best defenses, breaches remain an inevitable possibility, making incident response a pivotal syllabus component. Candidates are guided through the structured processes of detecting, analyzing, and containing security incidents. They learn how to minimize damage, preserve forensic evidence, and communicate effectively with stakeholders during crises.
Recovery strategies follow, emphasizing how organizations restore normal operations without leaving vulnerabilities unaddressed. This includes patching exploited weaknesses, revisiting security policies, and training users to prevent recurrence. The syllabus frames incident response as both reactive and proactive, highlighting its cyclical nature—each event becomes a learning opportunity that strengthens future resilience. Candidates thus develop a mindset that values preparedness, adaptability, and continuous improvement.
Systematic Preparation Through Modular Study
The syllabus not only outlines topics; it implicitly suggests how learners should approach them. Dividing the content into distinct modules fosters focus and clarity. By tackling each domain individually—whether network fundamentals, encryption, authentication, or incident management—candidates can build a layered understanding rather than grappling with overwhelming complexity.
Practical reinforcement complements theoretical study. Sample questions, simulated scenarios, and real-world exercises transform abstract principles into tangible skills. This iterative process of learning, practicing, and revisiting ensures that knowledge is embedded deeply rather than fading after superficial review. The modular strategy reflects the syllabus itself: a methodical construction of expertise, piece by piece, until a comprehensive mastery emerges.
Integrating Theory with Professional Application
While the syllabus serves as an academic guide, its relevance extends far beyond examination halls. Candidates are encouraged to view each component not merely as content to memorize but as professional tools to wield. Secure network design, encryption, and authentication mechanisms are daily realities for those working in digital ecosystems. Recognizing their application bridges the gap between academic success and workplace proficiency.
The syllabus fosters this integration by framing every concept in terms of both defense and practicality. A candidate who comprehends role-based access control not only answers questions accurately but also configures systems responsibly in real contexts. By weaving real-world significance into its structure, the syllabus ensures candidates emerge not just as exam-ready individuals but as practitioners capable of navigating and fortifying evolving digital terrains.
This integration cultivates a professional mindset where theory is never isolated from application. For instance, when a candidate studies encryption algorithms, the learning extends beyond understanding mathematical foundations. It includes recognizing the environments in which specific algorithms should be deployed, how they safeguard sensitive transmissions, and the limitations that dictate when alternatives may be required. Such practical discernment cannot be acquired through rote learning alone; it emerges from perceiving theory as a guide to authentic challenges.
The same principle applies to network defenses. A syllabus module on firewalls may outline rules, packet inspection, or proxy configurations, but the real mastery comes when a professional adapts these mechanisms to organizational needs. Consider a scenario where an enterprise faces persistent intrusion attempts—merely knowing the textbook definition of intrusion detection is insufficient. What matters is applying this knowledge to design layered defenses, deploy monitoring systems, and respond to alerts with precision. Here, academic preparation directly informs tangible decision-making.
Furthermore, the syllabus encourages ethical responsibility alongside technical mastery. Cybersecurity professionals often encounter dilemmas where decisions must balance convenience, cost, and confidentiality. By embedding discussions of access control, governance, and compliance within its framework, the syllabus prepares candidates to make judgments rooted not only in technical viability but also in accountability. A professional who understands the significance of regulatory frameworks like data protection laws will apply principles responsibly, ensuring both compliance and trustworthiness.
Another aspect of integration lies in incident response preparation. The syllabus equips learners with theoretical knowledge about threat detection and containment strategies, but its true value is realized when professionals face the urgency of a live breach. The ability to stay composed, analyze logs, trace intrusions, and mitigate damage stems from internalizing theory and practicing its execution under pressure. Candidates who grasp this synergy develop resilience, an attribute highly prized in modern cybersecurity roles.
Collaboration also gains prominence through this integrative approach. Cybersecurity rarely operates in isolation; it thrives on interdisciplinary interaction with developers, administrators, and leadership teams. The syllabus, by covering principles of secure coding, policy creation, and user awareness, ensures candidates appreciate the broader ecosystem in which they function. This translates into professionals who can communicate technical details in accessible terms, influence security culture, and advocate effectively for organizational safeguards.
Lastly, integrating theory with practice fuels innovation. When professionals understand core concepts deeply, they are not bound by predefined solutions. Instead, they can adapt frameworks creatively, tailoring defenses to novel threats. This capacity to innovate arises from seeing theory not as rigid doctrine but as a foundation for experimentation and problem-solving. Professionals equipped with such adaptability are those who thrive in a landscape defined by ever-shifting cyber risks.
In sum, the syllabus becomes far more than an exam blueprint—it becomes a blueprint for professional excellence. Candidates who engage with its content as living principles rather than static knowledge emerge as versatile, responsible, and forward-thinking practitioners. This seamless integration of theory with application ensures that the transition from classroom to workplace is not abrupt but fluid, empowering individuals to safeguard digital landscapes with confidence and ingenuity.
Understanding the CIW 1D0-571 Exam Code
The CIW 1D0-571 exam is officially titled CIW Web Security Associate. Its code, 1D0-571, identifies it within the CIW (Certified Internet Web Professional) certification family. Unlike generic security examinations, the CIW 1D0-571 concentrates on securing websites, web servers, and online communications, making it highly relevant for professionals in network administration, development, and security analysis. The code itself serves as a unique identifier, differentiating this credential from other CIW pathways such as design, networking, or database certifications.
Candidates pursuing the 1D0-571 are evaluated across a comprehensive set of domains: security principles, authentication methods, encryption protocols, common attack strategies, firewall implementation, intrusion detection, and best practices for secure online communication. The structure of the exam requires individuals to navigate ninety questions within ninety minutes, demanding not only knowledge but also efficiency. By mastering the specifics of the exam code, aspirants situate themselves firmly within the cybersecurity niche, signaling their preparedness for roles where safeguarding digital assets is paramount.
Why Practice Tests Matter for Exam Code 1D0-571
The nature of the CIW 1D0-571 exam is both technical and scenario-driven, meaning it is not enough to simply memorize definitions. Practice tests for this exam code serve as precision tools that replicate the actual environment. They are designed to emulate question phrasing, difficulty levels, and distribution across topics. This simulation acclimates candidates to the flow of the exam, reducing surprises and improving adaptability.
Moreover, the use of practice tests ensures alignment with the official objectives mapped to exam code 1D0-571. Each question category corresponds directly with the certification blueprint, allowing learners to measure their preparedness against the exact expectations. This alignment is crucial because it transforms preparation from guesswork into targeted readiness. A candidate who invests in consistent practice under exam conditions gradually masters not only the content but also the subtle art of navigating the exam code’s intricacies.
Time Mastery through Simulated Drills
The CIW 1D0-571 allows ninety minutes to conquer ninety questions, meaning candidates are required to maintain an average of one minute per question. This demands sharp time allocation and disciplined pacing. Practice tests create an environment where learners rehearse this very rhythm, training themselves to move seamlessly between straightforward queries and intricate scenario-based problems.
Initially, candidates may find themselves overwhelmed, devoting too much time to complex items while neglecting simpler ones. However, repeated exposure to practice simulations instills discipline. Candidates gradually learn to triage questions, answering those they know immediately while bookmarking more challenging ones for later review. Over time, this pacing evolves into second nature, enabling candidates to move fluidly through the exam code’s demands without panic.
Easing the Psychological Burden
The CIW 1D0-571 can appear intimidating, especially for those attempting their first certification. Anxiety, if left unchecked, may erode performance even among knowledgeable candidates. Practice tests act as a psychological balm, transforming fear into familiarity. Each repetition reduces uncertainty by simulating the testing interface, question style, and intensity of time pressure.
As familiarity grows, anxiety diminishes. The candidate enters the actual exam with an inner sense of déjà vu, as if stepping into a space already navigated many times before. This comfort fosters calmness, and calmness sharpens clarity. Thus, practice tests are not merely about intellectual preparation—they are tools of emotional conditioning, sculpting composure under the gaze of the exam clock.
Spotting Weaknesses with Surgical Precision
The exam code 1D0-571 encompasses broad yet intricate domains: encryption, firewalls, intrusion detection, secure communication, and the anatomy of web-based attacks. Without practice tests, candidates may not realize where their knowledge falters until it is too late. These tests act like diagnostic instruments, pinpointing weak spots with surgical accuracy.
Perhaps a candidate consistently falters on encryption algorithms, misinterpreting the distinctions between symmetric and asymmetric methods. Another may stumble when asked to identify the mechanics of a denial-of-service attack. Practice tests expose these vulnerabilities clearly, urging learners to recalibrate their focus. This targeted reinforcement ensures preparation is not shallow but strategic, repairing cracks before the final performance.
The Iterative Cycle of Mastery
Mastery of the CIW 1D0-571 is not born from a single reading or one round of revision. It emerges from an iterative cycle: study, practice, evaluate, revise, repeat. Practice tests are the heartbeat of this cycle. Each attempt deepens familiarity, uncovers blind spots, and measures progress against previous efforts.
The spiral of mastery works by layering knowledge. In the early stages, practice tests may feel overwhelming. Yet over successive rounds, patterns begin to emerge, confidence takes root, and performance improves. With every loop through the cycle, the candidate draws closer to mastery—less guessing, more certainty; less hesitation, more fluidity. This cyclical preparation embodies the very nature of professional growth.
Sharpening Analytical Thinking
The 1D0-571 is not a memory-based exam. It tests the ability to analyze real-world security scenarios. For example, candidates might be presented with a description of a phishing attempt or the signs of an SQL injection attack and asked to determine the best countermeasure. Practice tests sharpen this analytical ability by repeatedly immersing learners in problem-solving exercises.
Each scenario forces candidates to move beyond recognition into reasoning, weighing different approaches, and applying theoretical principles in dynamic contexts. Through this repeated analytical engagement, candidates transform into agile thinkers capable of not just passing the exam but also thriving in professional environments where security threats are constantly evolving.
Building Confidence through Consistency
Confidence is rarely a gift of chance; it is cultivated through repetition. Every practice test completed adds another layer of assurance. Success on these simulated exams plants seeds of self-belief, while failures illuminate areas needing further refinement. Together, they build a consistent foundation.
This steady rhythm of practice yields a psychological transformation. The candidate who once approached the exam with trepidation begins to view it as a conquerable challenge. By the time the actual 1D0-571 exam arrives, the candidate is no longer walking into an unknown arena but stepping into familiar territory with a calm, collected spirit.
Practice Tests as Precision Instruments
In the realm of preparation, not all tools hold equal value. Textbooks provide knowledge, lectures give context, but practice tests offer precision. They measure preparedness with exactness, highlighting the boundary between what is known and what remains uncertain. For the 1D0-571, where every question matters in the ninety-minute window, such precision can be the difference between success and failure.
When practice tests are approached with discipline, they evolve from mere simulations into instruments of refinement. Each incorrect answer transforms into a micro-lesson;, each correct one reinforces certainty. The result is a candidate equipped not only with theoretical understanding but with practical readiness honed to razor-sharp precision.
The Symbiotic Relationship of Competence and Confidence
Competence without confidence falters under pressure, while confidence without competence collapses when tested by rigor. Practice tests forge a symbiotic relationship between the two. They cultivate competence through exposure and analysis, while simultaneously instilling confidence by demonstrating measurable improvement.
As this relationship matures, candidates embody both intellectual strength and psychological steadiness. It is this union that leads to not just passing scores but commanding performances. In professional life, the same synergy proves invaluable, as web security specialists must balance technical expertise with the calmness to act decisively under real-world stress.
Transcending the Exam: Skills for a Career
Though the immediate goal of practice tests is success on the CIW 1D0-571 exam, their impact transcends the examination room. The very habits cultivated through disciplined practice—time management, strategic thinking, iterative learning, and calm under pressure—mirror the skills required of cybersecurity professionals.
In workplaces where threats evolve daily, professionals must analyze, adapt, and respond rapidly. The preparation journey for the exam code thus doubles as a rehearsal for professional reality. Each simulated test is a training ground, shaping the candidate into a practitioner capable of defending digital environments with precision and foresight.
Earning the CIW Web Security Associate certification signifies more than just technical proficiency; it signals a deliberate step into one of the most dynamic and indispensable spheres of the digital era. In a climate where cyber threats constantly evolve, professionals who can safeguard networks, systems, and web applications are considered invaluable. This certification functions as both a validation of expertise and a springboard toward an expansive range of professional opportunities, financial rewards, and personal enrichment.
Expanding Employment Horizons
One of the most immediate and tangible rewards of achieving this credential is the widening of professional pathways. Web security has emerged as a non-negotiable priority for enterprises of every scale, from start-ups to multinational conglomerates. Certified individuals are perceived as more than just technically adept; they are regarded as reliable custodians of digital assets. Employers seeking trustworthy defenders of their infrastructures often prefer candidates with verifiable certifications, allowing them to bypass concerns about untested knowledge or shallow skill sets.
For aspirants entering the workforce, the certification becomes an accelerant, propelling them toward positions that may otherwise require years of experience. For seasoned professionals, it operates as a differentiator, setting them apart from peers who may rely solely on practical experience without formal validation. In either case, the credential acts as a silent advocate, opening doors to interviews, promotions, and specialized assignments that reward demonstrated competence.
Elevating Compensation Potential
With specialized expertise comes elevated financial recognition. Organizations consistently allocate higher budgets for positions that involve the protection of their digital infrastructures, and certification provides tangible proof of capability. Professionals bearing this credential often find themselves eligible for roles with generous remuneration packages, performance incentives, and rapid salary progression.
The financial impact extends beyond base pay. Certified individuals often command greater negotiating power during hiring discussions or annual reviews. Employers are aware of the risks and potential costs associated with weak security postures, making them more willing to invest in individuals who bring verified knowledge to the table. For many, this translates not just into higher paychecks but also into a sense of professional security in an ever-volatile job market.
Broadening Career Roles and Specializations
Web security is not a monolithic discipline; it encompasses a broad range of roles, each with unique responsibilities and trajectories. A CIW-certified professional can pursue avenues such as web security analyst, network security specialist, vulnerability assessor, penetration testing consultant, or incident response coordinator. Each position offers distinct challenges and learning opportunities, allowing professionals to carve a personalized niche within the cybersecurity ecosystem.
This breadth also ensures long-term sustainability of the career path. Unlike fields that risk obsolescence due to automation, web security thrives on constant adaptation. New attack vectors, regulatory mandates, and technological innovations ensure a continuous demand for skilled professionals. Certification becomes the bedrock upon which diverse, evolving, and resilient career journeys can be built.
Strengthening Professional Credibility
Credibility is a currency that governs advancement in competitive industries. Holding a CIW Web Security Associate credential demonstrates not only technical mastery but also an enduring commitment to professional development. Employers, colleagues, and clients interpret the certification as evidence of diligence, self-discipline, and forward-thinking motivation.
This credibility often translates into heightened trust. Colleagues may be more inclined to seek the certified professional’s counsel during critical projects, while leadership may view them as reliable stewards of sensitive initiatives. Over time, such recognition can mature into leadership opportunities, management roles, or invitations to spearhead strategic security programs.
Enhancing Networking Opportunities
A less tangible but equally potent advantage lies in the expanded network of professionals gained through certification. Becoming part of a certified community exposes individuals to forums, conferences, mentorship circles, and collaborative projects. These interactions can spark new ideas, refine skill sets, and create pathways toward unanticipated career ventures.
Networking also provides a form of resilience in uncertain times. Should economic shifts or organizational restructuring occur, having a vibrant professional community offers lifelines to new opportunities. The connections made through certification circles often transcend geographical boundaries, opening access to global perspectives, international projects, and cross-cultural collaborations in the realm of cybersecurity.
Fueling Personal Growth and Intellectual Enrichment
Beyond its professional implications, the certification journey fosters profound personal development. Preparing for the examination requires disciplined study, rigorous practice, and consistent engagement with evolving concepts in security. These efforts sharpen problem-solving capabilities, enhance analytical reasoning, and cultivate meticulous attention to detail.
Such traits are not confined to cybersecurity alone; they spill into everyday decision-making, project management, and interpersonal interactions. Certified professionals often report a heightened ability to think strategically under pressure, adapt swiftly to unforeseen challenges, and approach complex problems with confidence. This intellectual resilience becomes a lifelong asset, enriching both professional and personal spheres.
Establishing Long-Term Career Security
In a world increasingly reliant on digital transactions, communication, and commerce, web security has evolved from a niche requirement into a global necessity. The demand for skilled professionals is unlikely to diminish; if anything, it will intensify. Holding a CIW Web Security Associate certification thus provides an element of insurance—a safeguard against obsolescence.
Professionals who adapt, renew, and deepen their expertise through certifications are less likely to face career stagnation. Instead, they position themselves as perpetual learners, continuously relevant in a marketplace where outdated skills can quickly erode opportunities. For many, this assurance of employability represents one of the most valuable benefits of the certification.
Building a Reputation as a Trusted Advisor
Over time, certified professionals often find themselves regarded not just as employees but as trusted advisors. Their insights into emerging threats, preventative measures, and strategic defense planning make them invaluable to organizations navigating complex security landscapes. This shift in perception—from executor to advisor—often unlocks higher levels of autonomy, influence, and respect.
Trusted advisors are invited into executive discussions, participate in shaping organizational policies, and influence broader digital strategies. For individuals with ambitions that extend beyond technical execution, certification provides a credible launchpad toward roles with greater strategic impact.
Creating Pathways for Leadership Development
As credibility, networking, and advisory roles expand, certified professionals naturally move closer to leadership opportunities. Supervisory positions, team management responsibilities, or even executive-level roles in cybersecurity become attainable. Certification signals not only technical proficiency but also the resilience, determination, and foresight required to guide others.
Those who aspire to mentor emerging talent or contribute to the shaping of organizational culture find certification invaluable. It represents the first formal step in transitioning from individual contributor to visionary leader, paving the way for a legacy that extends beyond personal achievement to the cultivation of future security professionals.
Sustaining Motivation Through Lifelong Learning
Cybersecurity is in perpetual flux, and certification cultivates an appetite for lifelong learning. The initial preparation process demonstrates how quickly knowledge can evolve and how essential it is to remain vigilant. This mindset, once ingrained, drives certified professionals to continuously refine their expertise, explore cutting-edge technologies, and anticipate the challenges of tomorrow.
This relentless pursuit of knowledge ensures that certified individuals remain not only employable but also indispensable. Their adaptability, curiosity, and foresight keep them at the forefront of innovation, making them catalysts for progress in their organizations and beyond.
Conclusion
The pursuit of the CIW Web Security Associate certification is more than an academic milestone; it represents a deliberate commitment to securing a profession in one of the most vital sectors of the digital age. By earning this credential, professionals do not simply acquire a title—they unlock a cascade of opportunities that extend from immediate job placement to long-term career resilience. The certification validates expertise, bolsters credibility, and grants access to a dynamic network of peers, each element converging to create a platform for enduring success.
What makes this achievement particularly powerful is its dual benefit: it nourishes both professional growth and personal evolution. The technical knowledge gained equips individuals to defend against complex threats, while the intellectual discipline required enhances strategic thinking, patience, and adaptability. This synthesis of hard and soft skills is what elevates certified professionals into trusted advisors, leaders, and innovators in their organizations.
As industries evolve and cyber risks become increasingly sophisticated, the demand for verified security expertise will continue to escalate. Holding the CIW Web Security Associate credential ensures that individuals remain relevant, competitive, and indispensable in this ever-changing arena. It serves as a beacon of reliability, signaling not only current competence but also future readiness to adapt and excel.
Ultimately, this certification is less about a single examination and more about embracing a lifelong journey of learning, leadership, and influence. It empowers professionals to build not just careers, but legacies—careers defined by trust, opportunity, and the unwavering ability to safeguard the digital world. Those who invest in this path are not merely preparing for jobs; they are positioning themselves at the forefront of a global movement to protect, preserve, and progress within the interconnected fabric of modern society.